Verizon DBIR 2025: Access is Still the Point of Failure
Verizon’s 2025 Data Breach Investigations Report (DBIR) reinforces a foundational truth: breaches begin at the point of initial access and most often through stolen credentials or exploited device vulnerabilities. And as always, the human element continues to leave security doors propped wide open.
Here’s a review of the key trends identified in the 18th annual DBIR report which evaluated over 20,000 security incidents and recommendations for effective mitigation strategies.
Credentials: The Primary Initial Access Vector
Attackers love credentials because they're predictable. They’re stolen, guessed, leaked in repositories, or extracted via infostealers. And in the 2025 DBIR, credential abuse remains the dominant vector across phishing, web attacks, and ransomware.
This last year, 22% of breaches began with credential abuse and 16% began with phishing. Additionally 88% of Basic Web Application attacks, a top attack pattern, involved stolen credentials.

Digging in one level deeper, within the broader category of social engineering (a top incident pattern), phishing remains king but prompt bombing has for the first time made the cut as a top action.

The Increasing Rise of Device Risks
A key point the report highlighted is that 20% of breaches began with exploited device vulnerabilities which is a 34% year over year increase while VPN-targeted exploits grew almost eight-fold.
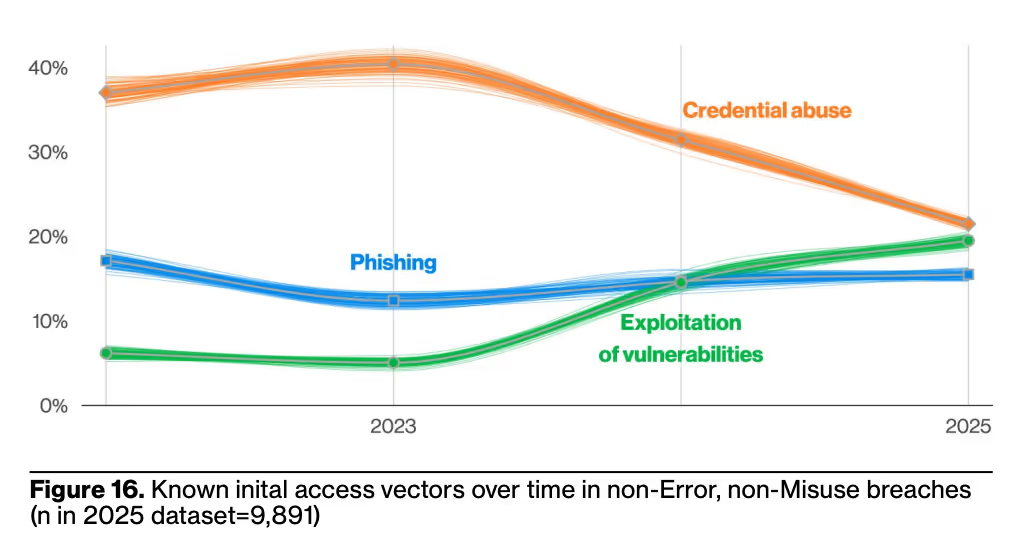
Additionally, 46% of the systems compromised with an infostealer that had possible corporate login data were non-managed devices. This led the report to politely call out that, “If you don’t choose to have a BYOD policy and don’t enforce what sorts of devices have access to corporate systems, the BYOD policy can wind up being chosen for you and you might not like the results.”

Our customer got it right when they say, “it’s not just my users that login, it’s also their devices.” Interested to see how Beyond Identity enables organizations to control access for unmanaged, contractor, and partner devices? Book your custom demo.
Human Risk Is Persistent…and Not Solved by Training
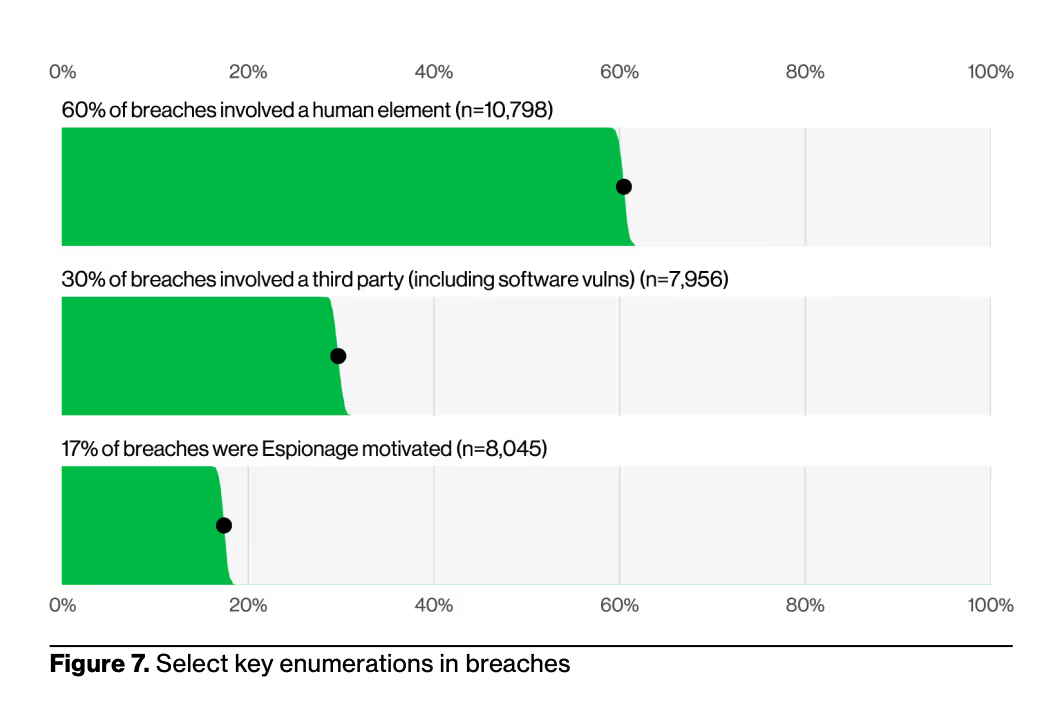
In the discussion of results, the report states, “Breaches involving humans were responsible for the majority of cases reviewed” (as opposed to automated exploit chains) with 60% of breaches involving the human element.
What’s more, despite user training and security awareness programs, people will still click. In fact, the researchers “found that the failure rate (aka the click rate) was unaffected by training”.

MFA Bypass Attacks Are Escalating in Frequency and Sophistication
Evidence shows that weak MFA, like ones that rely on phishable methods including one-time codes (OTP), number match, and push notifications, is being bypassed at scale.
This year’s DBIR documents a surge in MFA bypass methods. In addition to prompt bombing, adversaries are successfully using:
- Token theft: Hijacking session cookies or tokens to bypass the MFA step
- MFA interrupt: Flooding the user with notifications until they accept
- Adversary-in-the-Middle (AiTM): Intercepting MFA prompts to gain access in real-time
These attacks are working and often leading directly to ransomware deployment, account takeovers, or lateral movement.

Interested in seeing how your MFA can be exploited? Book your personalized demo with one of our security experts today.
Third-Party Risk Climbs
Third-party risk made a strong appearance in this year’s DBIR, with breaches involving external partners doubling year-over-year, now accounting for 30% of all breaches (up from 15% in 2024). These incidents weren’t limited to software supply chain vulnerabilities; they included credential exposures from partners, misconfigured SaaS environments, and a lack of secure-by-default settings. This prompted researchers to advise, “Secure-by-default standards on those platforms make a significant difference in the security bottom line”.
Beyond Identity’s Perspective: Eliminate Access Risks at the Root
Every year we review the DBIR and a surprising conclusion we come to is: while new threats are added annually, the existing threats around credentials and devices persistently remain. This is a sobering reminder that bad actors evolve quickly and a call to action for defenders to keep up.
At Beyond Identity, we have a straightforward perspective. It’s not enough to detect and respond to incidents and breaches. You must be enabled to stop them at the source. That means:
- Eliminating weak credentials like passwords, one-time codes, push notifications, and other phishable methods of authentication. They are child’s play for bad actors to steal, purchase, and exploit.
- Deploy passwordless, phishing-resistant, device-bound MFA universally to eliminate credential-based initial access vectors and MFA bypass attacks
- Enforce device trust for both managed and unmanaged devices because attackers will always take the path of least resistance so you need to make sure every device that accesses corporate resources are secure, patched, and authorized
- Continuously assess user and device risk with real-time risk signals. Risk changes over time. Your defense must adapt to them.
Ultimately, your access decisions should be made on and enforced by your security policies, not based on human behavior.
See how Beyond Identity stops credential and device-based attacks before they begin. Book your demo here.
Verizon’s 2025 Data Breach Investigations Report (DBIR) reinforces a foundational truth: breaches begin at the point of initial access and most often through stolen credentials or exploited device vulnerabilities. And as always, the human element continues to leave security doors propped wide open.
Here’s a review of the key trends identified in the 18th annual DBIR report which evaluated over 20,000 security incidents and recommendations for effective mitigation strategies.
Credentials: The Primary Initial Access Vector
Attackers love credentials because they're predictable. They’re stolen, guessed, leaked in repositories, or extracted via infostealers. And in the 2025 DBIR, credential abuse remains the dominant vector across phishing, web attacks, and ransomware.
This last year, 22% of breaches began with credential abuse and 16% began with phishing. Additionally 88% of Basic Web Application attacks, a top attack pattern, involved stolen credentials.

Digging in one level deeper, within the broader category of social engineering (a top incident pattern), phishing remains king but prompt bombing has for the first time made the cut as a top action.

The Increasing Rise of Device Risks
A key point the report highlighted is that 20% of breaches began with exploited device vulnerabilities which is a 34% year over year increase while VPN-targeted exploits grew almost eight-fold.

Additionally, 46% of the systems compromised with an infostealer that had possible corporate login data were non-managed devices. This led the report to politely call out that, “If you don’t choose to have a BYOD policy and don’t enforce what sorts of devices have access to corporate systems, the BYOD policy can wind up being chosen for you and you might not like the results.”

Our customer got it right when they say, “it’s not just my users that login, it’s also their devices.” Interested to see how Beyond Identity enables organizations to control access for unmanaged, contractor, and partner devices? Book your custom demo.
Human Risk Is Persistent…and Not Solved by Training
In the discussion of results, the report states, “Breaches involving humans were responsible for the majority of cases reviewed” (as opposed to automated exploit chains) with 60% of breaches involving the human element.
What’s more, despite user training and security awareness programs, people will still click. In fact, the researchers “found that the failure rate (aka the click rate) was unaffected by training”.

MFA Bypass Attacks Are Escalating in Frequency and Sophistication
Evidence shows that weak MFA, like ones that rely on phishable methods including one-time codes (OTP), number match, and push notifications, is being bypassed at scale.
This year’s DBIR documents a surge in MFA bypass methods. In addition to prompt bombing, adversaries are successfully using:
- Token theft: Hijacking session cookies or tokens to bypass the MFA step
- MFA interrupt: Flooding the user with notifications until they accept
- Adversary-in-the-Middle (AiTM): Intercepting MFA prompts to gain access in real-time
These attacks are working and often leading directly to ransomware deployment, account takeovers, or lateral movement.

Interested in seeing how your MFA can be exploited? Book your personalized demo with one of our security experts today.
Third-Party Risk Climbs
Third-party risk made a strong appearance in this year’s DBIR, with breaches involving external partners doubling year-over-year, now accounting for 30% of all breaches (up from 15% in 2024). These incidents weren’t limited to software supply chain vulnerabilities; they included credential exposures from partners, misconfigured SaaS environments, and a lack of secure-by-default settings. This prompted researchers to advise, “Secure-by-default standards on those platforms make a significant difference in the security bottom line”.

Beyond Identity’s Perspective: Eliminate Access Risks at the Root
Every year we review the DBIR and a surprising conclusion we come to is: while new threats are added annually, the existing threats around credentials and devices persistently remain. This is a sobering reminder that bad actors evolve quickly and a call to action for defenders to keep up.
At Beyond Identity, we have a straightforward perspective. It’s not enough to detect and respond to incidents and breaches. You must be enabled to stop them at the source. That means:
- Eliminating weak credentials like passwords, one-time codes, push notifications, and other phishable methods of authentication. They are child’s play for bad actors to steal, purchase, and exploit.
- Deploy passwordless, phishing-resistant, device-bound MFA universally to eliminate credential-based initial access vectors and MFA bypass attacks
- Enforce device trust for both managed and unmanaged devices because attackers will always take the path of least resistance so you need to make sure every device that accesses corporate resources are secure, patched, and authorized
- Continuously assess user and device risk with real-time risk signals. Risk changes over time. Your defense must adapt to them.
Ultimately, your access decisions should be made on and enforced by your security policies, not based on human behavior.
See how Beyond Identity stops credential and device-based attacks before they begin. Book your demo here.
Verizon’s 2025 Data Breach Investigations Report (DBIR) reinforces a foundational truth: breaches begin at the point of initial access and most often through stolen credentials or exploited device vulnerabilities. And as always, the human element continues to leave security doors propped wide open.
Here’s a review of the key trends identified in the 18th annual DBIR report which evaluated over 20,000 security incidents and recommendations for effective mitigation strategies.
Credentials: The Primary Initial Access Vector
Attackers love credentials because they're predictable. They’re stolen, guessed, leaked in repositories, or extracted via infostealers. And in the 2025 DBIR, credential abuse remains the dominant vector across phishing, web attacks, and ransomware.
This last year, 22% of breaches began with credential abuse and 16% began with phishing. Additionally 88% of Basic Web Application attacks, a top attack pattern, involved stolen credentials.

Digging in one level deeper, within the broader category of social engineering (a top incident pattern), phishing remains king but prompt bombing has for the first time made the cut as a top action.

The Increasing Rise of Device Risks
A key point the report highlighted is that 20% of breaches began with exploited device vulnerabilities which is a 34% year over year increase while VPN-targeted exploits grew almost eight-fold.

Additionally, 46% of the systems compromised with an infostealer that had possible corporate login data were non-managed devices. This led the report to politely call out that, “If you don’t choose to have a BYOD policy and don’t enforce what sorts of devices have access to corporate systems, the BYOD policy can wind up being chosen for you and you might not like the results.”

Our customer got it right when they say, “it’s not just my users that login, it’s also their devices.” Interested to see how Beyond Identity enables organizations to control access for unmanaged, contractor, and partner devices? Book your custom demo.
Human Risk Is Persistent…and Not Solved by Training
In the discussion of results, the report states, “Breaches involving humans were responsible for the majority of cases reviewed” (as opposed to automated exploit chains) with 60% of breaches involving the human element.
What’s more, despite user training and security awareness programs, people will still click. In fact, the researchers “found that the failure rate (aka the click rate) was unaffected by training”.

MFA Bypass Attacks Are Escalating in Frequency and Sophistication
Evidence shows that weak MFA, like ones that rely on phishable methods including one-time codes (OTP), number match, and push notifications, is being bypassed at scale.
This year’s DBIR documents a surge in MFA bypass methods. In addition to prompt bombing, adversaries are successfully using:
- Token theft: Hijacking session cookies or tokens to bypass the MFA step
- MFA interrupt: Flooding the user with notifications until they accept
- Adversary-in-the-Middle (AiTM): Intercepting MFA prompts to gain access in real-time
These attacks are working and often leading directly to ransomware deployment, account takeovers, or lateral movement.

Interested in seeing how your MFA can be exploited? Book your personalized demo with one of our security experts today.
Third-Party Risk Climbs
Third-party risk made a strong appearance in this year’s DBIR, with breaches involving external partners doubling year-over-year, now accounting for 30% of all breaches (up from 15% in 2024). These incidents weren’t limited to software supply chain vulnerabilities; they included credential exposures from partners, misconfigured SaaS environments, and a lack of secure-by-default settings. This prompted researchers to advise, “Secure-by-default standards on those platforms make a significant difference in the security bottom line”.

Beyond Identity’s Perspective: Eliminate Access Risks at the Root
Every year we review the DBIR and a surprising conclusion we come to is: while new threats are added annually, the existing threats around credentials and devices persistently remain. This is a sobering reminder that bad actors evolve quickly and a call to action for defenders to keep up.
At Beyond Identity, we have a straightforward perspective. It’s not enough to detect and respond to incidents and breaches. You must be enabled to stop them at the source. That means:
- Eliminating weak credentials like passwords, one-time codes, push notifications, and other phishable methods of authentication. They are child’s play for bad actors to steal, purchase, and exploit.
- Deploy passwordless, phishing-resistant, device-bound MFA universally to eliminate credential-based initial access vectors and MFA bypass attacks
- Enforce device trust for both managed and unmanaged devices because attackers will always take the path of least resistance so you need to make sure every device that accesses corporate resources are secure, patched, and authorized
- Continuously assess user and device risk with real-time risk signals. Risk changes over time. Your defense must adapt to them.
Ultimately, your access decisions should be made on and enforced by your security policies, not based on human behavior.
See how Beyond Identity stops credential and device-based attacks before they begin. Book your demo here.

.avif)










.avif)
.avif)
.avif)



.avif)






.avif)

