Simply secure access for the age of zero trust







Workforce Secure Access is here
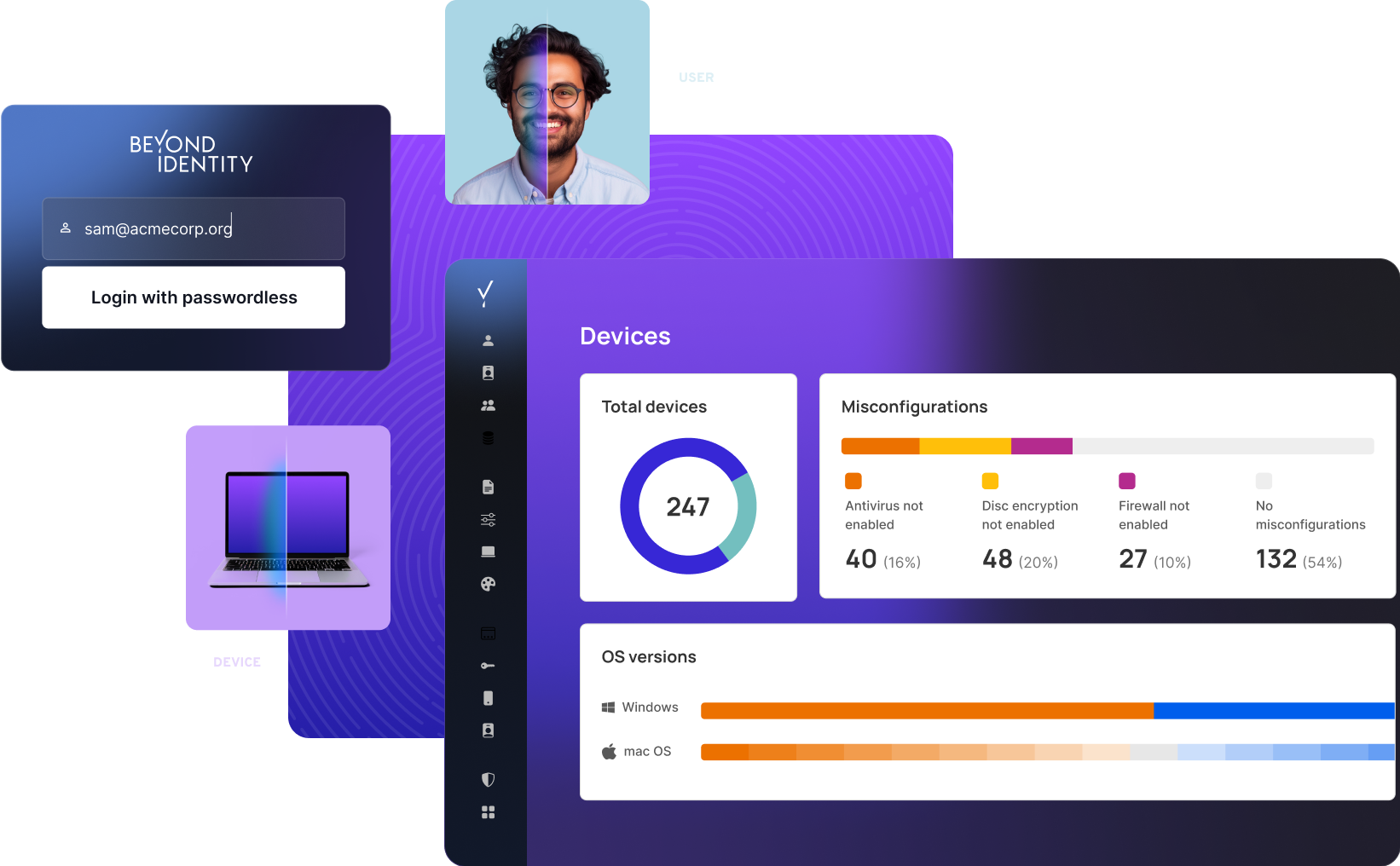
From risk discovery, to device posture, to SSO and beyond: learn how we’re helping teams like yours better than ever before.
Beyond secure. Beyond easy.
Beyond what you’d expect.










For modern teams and modern risks
















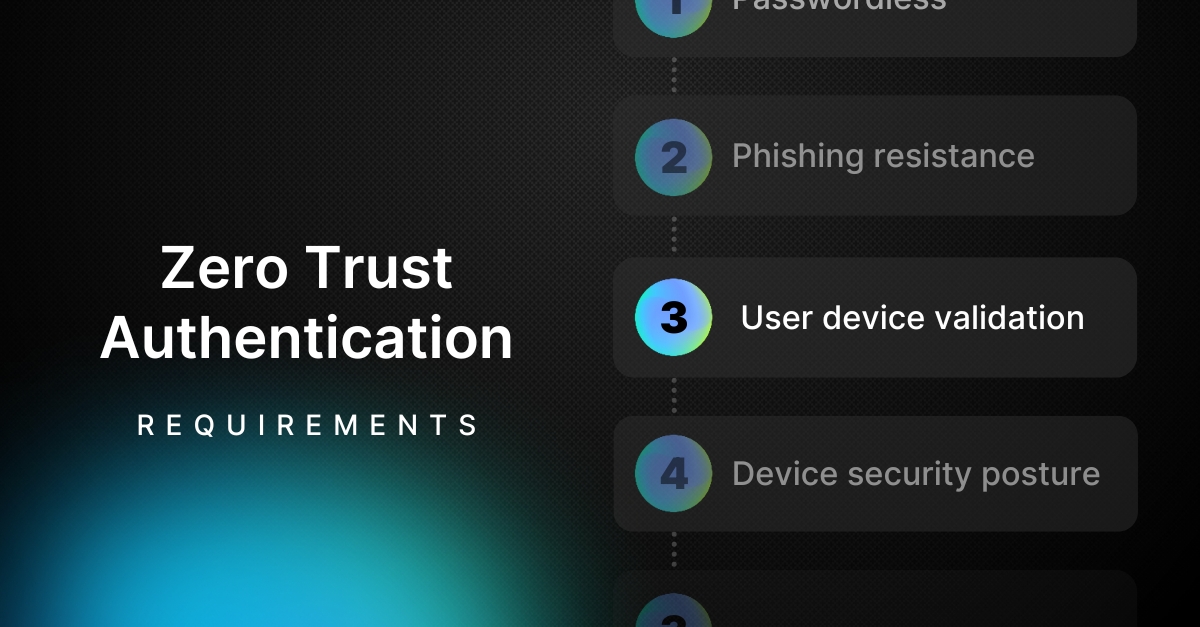
It’s time we re-booted on identity and access management
Whatever your challenge,
we’re in your corner


Eliminate phishing by removing shared secrets and other risky factors from the auth equation.
Learn more
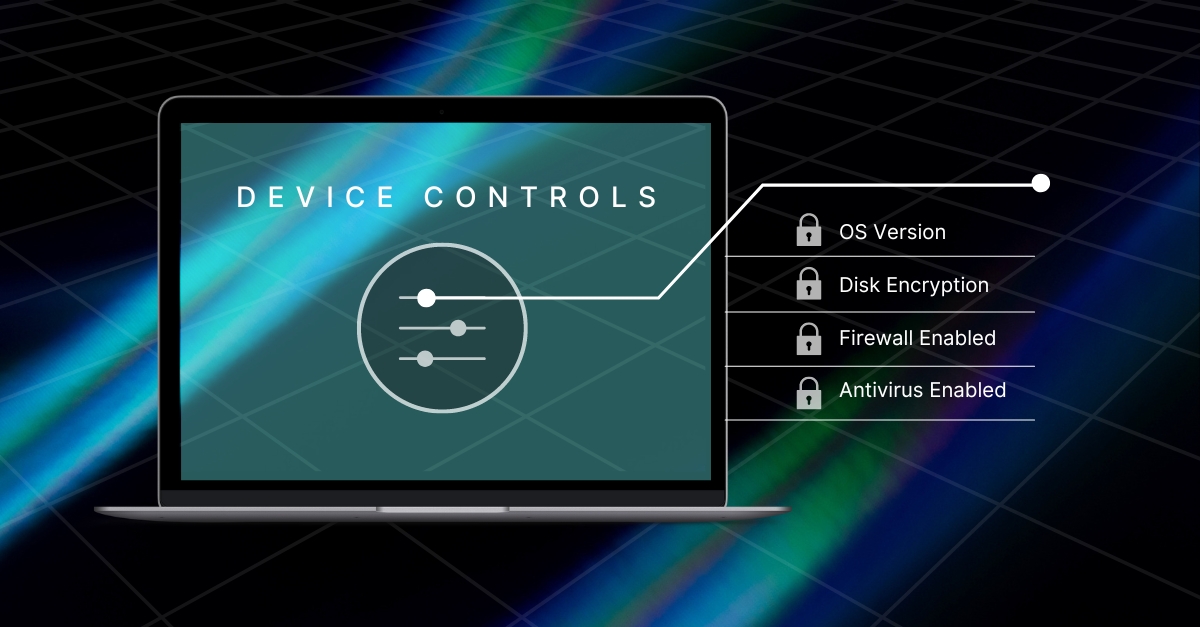
device security
Ensure that all devices are compliant with your security policies prior to granting access.
Learn more
Validate security controls at time of authentication and continuously re-check.
Learn more
acquisitions risk
Simplify security during transition with control over identity lifecycle, access, and device security.
Learn more
Easily meet and exceed regulations and cyber insurance requirements.
Learn more
Prevent and flag AI impersonation attacks and deepfakes targeting critical communication systems.
Learn more
Unite IT and security teams with a platform that simplifies workflows for both.
Learn moreLatest news and insights





Ready to take your team Beyond?
Schedule a call with a Beyond Identity expert.















.jpg)