Phishing 101
Learn from our extensive collection of information on phishing

What is "phish-resistant"?
Explore what the definition of "phish-resistant" is.

SSO Exploits: Ping One + PingFed Push
Explore a session hijack where Ping One SSO with PingFed 2FA push as a second factor is exploited.

SSO Exploits: Okta SSO + TOTP
Explore a session hijack scenario where Okta SSO with Okta Verify TOTP as a second factor is exploited.

SSO Exploits: Okta SSO + SMS
Explore a session hijack scenario where Okta SSO with Okta Verify SMS as a second factor is exploited.

SSO Exploits: Okta SSO + Push
Explore a session hijack scenario where Okta SSO with Okta Verify Push as a second factor is exploited.

SSO Exploits: Okta SSO + Duo Biometrics
Explore a session hijack scenario where Okta SSO with Okta Verify SMS as a second factor is exploited.

SSO Exploits: Okta SSO + Duo + Yubikey
Explore a session hijack scenario where Okta SSO with Duo + Yubikey as a second factor is exploited.

SSO Exploits: Okta Fastpass Insecure Launch
Explore a session hijack where Okta Fastpass is launched with an insecure launch mechanism.
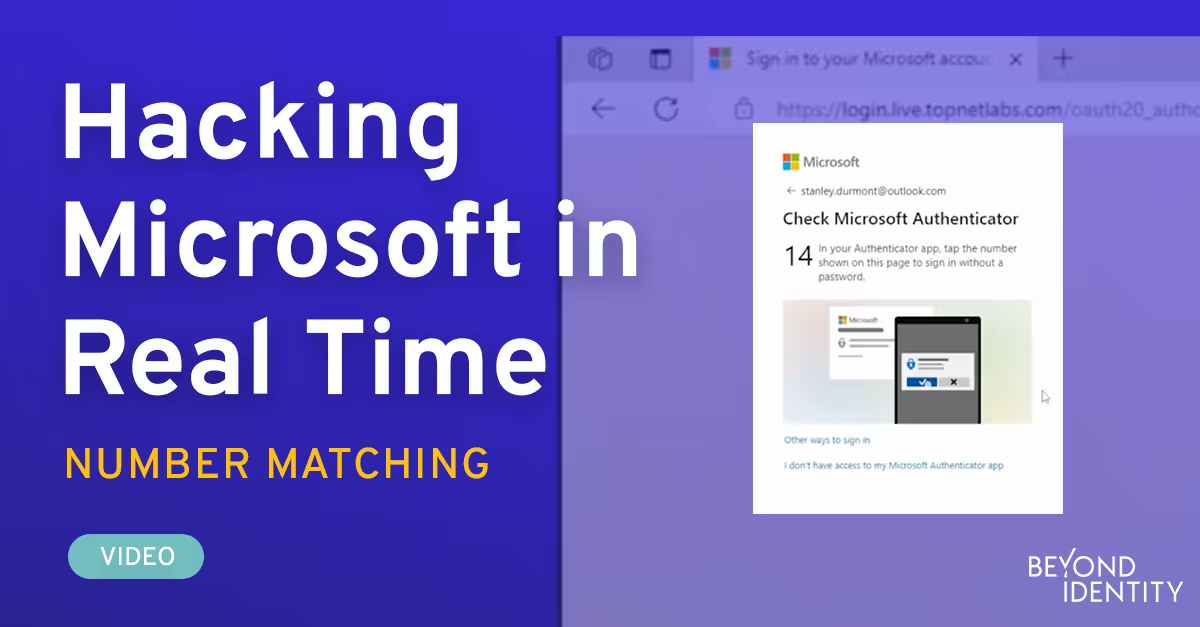
SSO Exploits: O365 + Number Matching
Explore a session hijack where Office 365 SSO with number matching as a second factor is exploited.

Phishable: TOTP
Explore why TOTP is phishable and common attacks on TOTP.

Phishable: SMS
Explore why SMS is phishable and common attacks on SMS.

Phishable: Push
Explore why Push is phishable and common attacks on Push.

