Why Your MFA Is Insecure
Multi-factor authentication (MFA) is designed to protect users and employees against account takeover attacks. However, piling multiple insecure authentication mechanisms on top of one another provides little real security. Many of the MFA solutions in place today still leave companies and their customers vulnerable to attack.
MFA is essential for the modern business
Account takeover attacks have been a threat for a while. Cybercriminals commonly use the access that they provide to steal data or deliver malware to corporate computers in Ransomware as a Service (RaaS) and other attacks. Account takeover attacks also target customers, enabling cybercriminals to use these accounts for fraud or to collect the personal information stored in these accounts, which can be invaluable for spear phishing and other social engineering attacks.
Without MFA and relying solely on passwords, it makes it much easier for hackers to infiltrate and have unfettered access to sensitive information. Using brute force attacks and credential stuffing, attackers can log in easily and undetected by security teams.
MFA can be an integral part of managing an organization’s risk of account takeover attacks. Effective MFA makes it more difficult for an attacker to access employee or customer accounts because they need to hack multiple factors. It is also commonly required for regulatory compliance. Some regulations, such as PCI DSS, mandate the use of MFA by employees with access to cardholder data.
While MFA has long been the go-to solution for companies when implementing security programs, it’s important to note that not all MFA is secure, and it often comes down to the factors being used in the authentication process.
Most MFA solutions are broken
Many businesses have already implemented MFA for their employees and customers, but not all MFA is created equal. In fact, common forms of MFA factors such as magic links, one-time passwords (OTPs), and push notifications provide little or no additional security beyond that of a password. And passwords, with the widespread use of weak and reused passwords and the threat of phishing attacks, are known to be one of the most hackable forms of user authentication and are often used as one of the factors in MFA.
Putting MFA in place is only marginally better than not implementing anything. The vast majority of deployed MFA solutions provide a false sense of security and are vulnerable to various exploits because of their insecure factors.
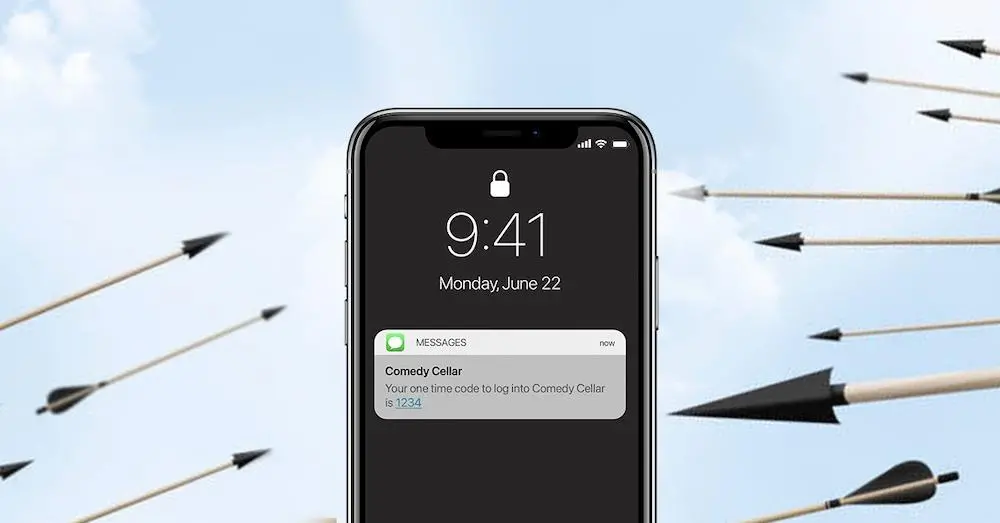
OTP interception
One of the most common forms of MFA is the use of OTPs. An SMS or email is sent to the user, who needs to type it into the login portal to authenticate. In theory, this provides additional protection because an attacker would need access to the user’s phone or email account to access the OTP.
In practice, an attacker can gain access to OTPs in multiple different ways. In a SIM swapping attack, the cybercriminal masquerades as the user to their mobile service provider and convinces them to switch service to a new attacker-owned SIM card. If successful, all OTPs will be sent to the attacker’s phone, enabling them to bypass MFA on all of the victim’s accounts.
For email-based MFA, the assumption is that the user’s email account is secure. If the email account uses the same password as the one targeted by the attacker, a cybercriminal could easily access both accounts and defeat the MFA.
Phishing attacks
Many forms of MFA require the user to take some action. This could include typing an OTP into a browser, approving access via a push notification, or clicking on a magic link.
The problem with these approaches is that they are all vulnerable to phishing attacks. A cybercriminal can trick a user into revealing an OTP or approving access in a push notification pop-up. Attackers have gotten better and better at sending alarming emails that make you click phishing links or serving login pages that look just like the real thing to get you to hand over the code you just received or to agree to sign off on a push notification.
Attackers could also use more sophisticated techniques, such as using Browser-in-the-Browser (BitB) exploits to serve nearly undetectable phishing pages to users. Once an attacker has phished the victim, they have access to the user’s account.
Password recovery exploits
Password reset functions are designed to allow a user to regain access to their account if they have lost or forgotten their password. This is accomplished by circumventing the normal authentication process and using other means to “authenticate” the user.
However, these password recovery processes are often vulnerable to attack. Sending magic links to the user’s email account or phone means that an email account takeover or SIM swapping attack provides complete access to a user’s online account. The answers to “secret” questions used during password resets are often publicly available on social media or other sources. Password recovery processes often undermine MFA by making the second factor (email, phone, etc.) the only thing that an attacker needs to access a user’s account.
Not All MFA is insecure (just the password-based ones)
Most MFA solutions are unsafe because they use phishable, insecure factors for authentication. Passwords have numerous issues, including password reuse and weak passwords. Other factors are vulnerable to SIM swapping, phishing, and other attacks. You can actually see how MFA can be phished in real time.
However, not all MFA factors are insecure. Biometric authentication (fingerprint scanning, facial recognition, etc.), device-level security checks, and similar factors provide greater usability and security than traditional, password-based authentication.
One of the main arguments for password plus OTP MFA is that it is easy to implement. However, the FIDO standards define methods to easily implement strong MFA. Businesses can require a combination of biometric authentication and device-specific private keys for MFA, rather than requiring users to enter a password and MFA code.
Implementing secure, passwordless MFA
Passwordless MFA that uses biometrics and device-specific private keys under the FIDO standard provides stronger, more usable authentication than other MFA solutions. With Beyond Identity, companies can quickly and easily roll out secure MFA to employees and customers. To see the benefits of passwordless, phishing-resistant MFA for yourself, get a free demo.
Multi-factor authentication (MFA) is designed to protect users and employees against account takeover attacks. However, piling multiple insecure authentication mechanisms on top of one another provides little real security. Many of the MFA solutions in place today still leave companies and their customers vulnerable to attack.
MFA is essential for the modern business
Account takeover attacks have been a threat for a while. Cybercriminals commonly use the access that they provide to steal data or deliver malware to corporate computers in Ransomware as a Service (RaaS) and other attacks. Account takeover attacks also target customers, enabling cybercriminals to use these accounts for fraud or to collect the personal information stored in these accounts, which can be invaluable for spear phishing and other social engineering attacks.
Without MFA and relying solely on passwords, it makes it much easier for hackers to infiltrate and have unfettered access to sensitive information. Using brute force attacks and credential stuffing, attackers can log in easily and undetected by security teams.
MFA can be an integral part of managing an organization’s risk of account takeover attacks. Effective MFA makes it more difficult for an attacker to access employee or customer accounts because they need to hack multiple factors. It is also commonly required for regulatory compliance. Some regulations, such as PCI DSS, mandate the use of MFA by employees with access to cardholder data.
While MFA has long been the go-to solution for companies when implementing security programs, it’s important to note that not all MFA is secure, and it often comes down to the factors being used in the authentication process.
Most MFA solutions are broken
Many businesses have already implemented MFA for their employees and customers, but not all MFA is created equal. In fact, common forms of MFA factors such as magic links, one-time passwords (OTPs), and push notifications provide little or no additional security beyond that of a password. And passwords, with the widespread use of weak and reused passwords and the threat of phishing attacks, are known to be one of the most hackable forms of user authentication and are often used as one of the factors in MFA.
Putting MFA in place is only marginally better than not implementing anything. The vast majority of deployed MFA solutions provide a false sense of security and are vulnerable to various exploits because of their insecure factors.
OTP interception
One of the most common forms of MFA is the use of OTPs. An SMS or email is sent to the user, who needs to type it into the login portal to authenticate. In theory, this provides additional protection because an attacker would need access to the user’s phone or email account to access the OTP.
In practice, an attacker can gain access to OTPs in multiple different ways. In a SIM swapping attack, the cybercriminal masquerades as the user to their mobile service provider and convinces them to switch service to a new attacker-owned SIM card. If successful, all OTPs will be sent to the attacker’s phone, enabling them to bypass MFA on all of the victim’s accounts.
For email-based MFA, the assumption is that the user’s email account is secure. If the email account uses the same password as the one targeted by the attacker, a cybercriminal could easily access both accounts and defeat the MFA.
Phishing attacks
Many forms of MFA require the user to take some action. This could include typing an OTP into a browser, approving access via a push notification, or clicking on a magic link.
The problem with these approaches is that they are all vulnerable to phishing attacks. A cybercriminal can trick a user into revealing an OTP or approving access in a push notification pop-up. Attackers have gotten better and better at sending alarming emails that make you click phishing links or serving login pages that look just like the real thing to get you to hand over the code you just received or to agree to sign off on a push notification.
Attackers could also use more sophisticated techniques, such as using Browser-in-the-Browser (BitB) exploits to serve nearly undetectable phishing pages to users. Once an attacker has phished the victim, they have access to the user’s account.
Password recovery exploits
Password reset functions are designed to allow a user to regain access to their account if they have lost or forgotten their password. This is accomplished by circumventing the normal authentication process and using other means to “authenticate” the user.
However, these password recovery processes are often vulnerable to attack. Sending magic links to the user’s email account or phone means that an email account takeover or SIM swapping attack provides complete access to a user’s online account. The answers to “secret” questions used during password resets are often publicly available on social media or other sources. Password recovery processes often undermine MFA by making the second factor (email, phone, etc.) the only thing that an attacker needs to access a user’s account.
Not All MFA is insecure (just the password-based ones)
Most MFA solutions are unsafe because they use phishable, insecure factors for authentication. Passwords have numerous issues, including password reuse and weak passwords. Other factors are vulnerable to SIM swapping, phishing, and other attacks. You can actually see how MFA can be phished in real time.
However, not all MFA factors are insecure. Biometric authentication (fingerprint scanning, facial recognition, etc.), device-level security checks, and similar factors provide greater usability and security than traditional, password-based authentication.
One of the main arguments for password plus OTP MFA is that it is easy to implement. However, the FIDO standards define methods to easily implement strong MFA. Businesses can require a combination of biometric authentication and device-specific private keys for MFA, rather than requiring users to enter a password and MFA code.
Implementing secure, passwordless MFA
Passwordless MFA that uses biometrics and device-specific private keys under the FIDO standard provides stronger, more usable authentication than other MFA solutions. With Beyond Identity, companies can quickly and easily roll out secure MFA to employees and customers. To see the benefits of passwordless, phishing-resistant MFA for yourself, get a free demo.
Multi-factor authentication (MFA) is designed to protect users and employees against account takeover attacks. However, piling multiple insecure authentication mechanisms on top of one another provides little real security. Many of the MFA solutions in place today still leave companies and their customers vulnerable to attack.
MFA is essential for the modern business
Account takeover attacks have been a threat for a while. Cybercriminals commonly use the access that they provide to steal data or deliver malware to corporate computers in Ransomware as a Service (RaaS) and other attacks. Account takeover attacks also target customers, enabling cybercriminals to use these accounts for fraud or to collect the personal information stored in these accounts, which can be invaluable for spear phishing and other social engineering attacks.
Without MFA and relying solely on passwords, it makes it much easier for hackers to infiltrate and have unfettered access to sensitive information. Using brute force attacks and credential stuffing, attackers can log in easily and undetected by security teams.
MFA can be an integral part of managing an organization’s risk of account takeover attacks. Effective MFA makes it more difficult for an attacker to access employee or customer accounts because they need to hack multiple factors. It is also commonly required for regulatory compliance. Some regulations, such as PCI DSS, mandate the use of MFA by employees with access to cardholder data.
While MFA has long been the go-to solution for companies when implementing security programs, it’s important to note that not all MFA is secure, and it often comes down to the factors being used in the authentication process.
Most MFA solutions are broken
Many businesses have already implemented MFA for their employees and customers, but not all MFA is created equal. In fact, common forms of MFA factors such as magic links, one-time passwords (OTPs), and push notifications provide little or no additional security beyond that of a password. And passwords, with the widespread use of weak and reused passwords and the threat of phishing attacks, are known to be one of the most hackable forms of user authentication and are often used as one of the factors in MFA.
Putting MFA in place is only marginally better than not implementing anything. The vast majority of deployed MFA solutions provide a false sense of security and are vulnerable to various exploits because of their insecure factors.
OTP interception
One of the most common forms of MFA is the use of OTPs. An SMS or email is sent to the user, who needs to type it into the login portal to authenticate. In theory, this provides additional protection because an attacker would need access to the user’s phone or email account to access the OTP.
In practice, an attacker can gain access to OTPs in multiple different ways. In a SIM swapping attack, the cybercriminal masquerades as the user to their mobile service provider and convinces them to switch service to a new attacker-owned SIM card. If successful, all OTPs will be sent to the attacker’s phone, enabling them to bypass MFA on all of the victim’s accounts.
For email-based MFA, the assumption is that the user’s email account is secure. If the email account uses the same password as the one targeted by the attacker, a cybercriminal could easily access both accounts and defeat the MFA.
Phishing attacks
Many forms of MFA require the user to take some action. This could include typing an OTP into a browser, approving access via a push notification, or clicking on a magic link.
The problem with these approaches is that they are all vulnerable to phishing attacks. A cybercriminal can trick a user into revealing an OTP or approving access in a push notification pop-up. Attackers have gotten better and better at sending alarming emails that make you click phishing links or serving login pages that look just like the real thing to get you to hand over the code you just received or to agree to sign off on a push notification.
Attackers could also use more sophisticated techniques, such as using Browser-in-the-Browser (BitB) exploits to serve nearly undetectable phishing pages to users. Once an attacker has phished the victim, they have access to the user’s account.
Password recovery exploits
Password reset functions are designed to allow a user to regain access to their account if they have lost or forgotten their password. This is accomplished by circumventing the normal authentication process and using other means to “authenticate” the user.
However, these password recovery processes are often vulnerable to attack. Sending magic links to the user’s email account or phone means that an email account takeover or SIM swapping attack provides complete access to a user’s online account. The answers to “secret” questions used during password resets are often publicly available on social media or other sources. Password recovery processes often undermine MFA by making the second factor (email, phone, etc.) the only thing that an attacker needs to access a user’s account.
Not All MFA is insecure (just the password-based ones)
Most MFA solutions are unsafe because they use phishable, insecure factors for authentication. Passwords have numerous issues, including password reuse and weak passwords. Other factors are vulnerable to SIM swapping, phishing, and other attacks. You can actually see how MFA can be phished in real time.
However, not all MFA factors are insecure. Biometric authentication (fingerprint scanning, facial recognition, etc.), device-level security checks, and similar factors provide greater usability and security than traditional, password-based authentication.
One of the main arguments for password plus OTP MFA is that it is easy to implement. However, the FIDO standards define methods to easily implement strong MFA. Businesses can require a combination of biometric authentication and device-specific private keys for MFA, rather than requiring users to enter a password and MFA code.
Implementing secure, passwordless MFA
Passwordless MFA that uses biometrics and device-specific private keys under the FIDO standard provides stronger, more usable authentication than other MFA solutions. With Beyond Identity, companies can quickly and easily roll out secure MFA to employees and customers. To see the benefits of passwordless, phishing-resistant MFA for yourself, get a free demo.








.jpg)
.jpg)
.jpg)

.jpg)
.jpg)



.jpeg)






.png)

