Stop Blaming Users For Their Insecure Passwords
Why are we still burdening users with the nearly impossible task of maintaining secure passwords?
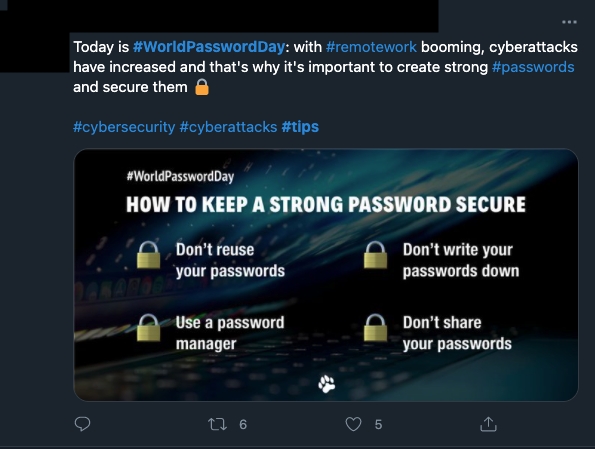
Passwords are fundamentally flawed for a number of reasons—they are difficult to keep safe, long and arduous to remember, and easily susceptible to breach or attack. Many organizations use World Password Day as a way to offer up some helpful tips, like these, on how to keep a password secure…
- “Use at least 15 characters”
- “Mix up letters and symbols”
- “Don’t use sequential numbers”
- “Avoid using personal information”
And more, to put the onus on the user to keep their personal information secure. Organizations will prompt users to change or update their passwords to “enhance security” and offer up these tips or requirements. But why aren’t we demanding the organization itself to investigate other, more secure forms of authentication? Try as you might to secure passwords, but they will always lack the security that a passwordless solution can provide. Here’s why some of these tips, while likely well intended, make little difference in improving security.
Frequently Given Tips That Don’t Work
Some of the most commonly recommended tips when it comes to passwords can be some of the most useless. There are many ways in which passwords can easily be breached or hacked, resulting in huge problems for your organization, even if you follow all the “best practices” for passwords. For example, much of the advice you will come across on the internet reminds the user to use long, strong passwords, such as using a combination of symbols and letters, not reusing previous passwords, and not making your password easy to guess, such as “p@ssword”, but even following this advice will not keep your password safe.
A password is a “shared secret”, meaning it is a piece of information known by both the user and the service provider, and as a result of this are fundamentally insecure because of the risk of being breached on either end. Most organizations put this blame entirely on the user, forcing them to regularly change their passwords, extend the length, and create a poor experience.
If your credentials are password-based, then they are stored in databases, and this is a huge problem for the security of your applications and systems. Databases are breached with alarming frequency, and no organization is safe—even Microsoft. It doesn’t matter if your password is 2,213 characters long and chock full of symbols. When a user is tricked by a phishing email, the complexity of their password is irrelevant. As long as passwords are being used, they will be stolen, because of their existence in multiple places and ability to be stolen or breached.
Unlike shared secrets, passwordless authentication eliminates passwords all together, leaving no credentials for hackers to snatch in the first place. Organizations need to take responsibility for authentication security and make the move beyond passwords.
The False Security of Password Managers
Another common piece of advice is to use a password manager. A password manager is, in essence, a way to store and generate your login information in an encrypted way to access applications, websites, and systems. What many people don’t realize is that password managers carry the same problems that passwords do. The password still exists, it is just hidden from the user. This may make it more convenient for the user but not any more secure.
- All your sensitive information is in one place, so the potential for damage caused by a hack is frightening to consider
- Your password manager has a password of its own
- Your password is still a shared secret but now its shared with one more party (the password manager)
The password manager is a solution designed by a system that wants to pass responsibility off to the user for breaches by assigning the safety of a password to the user. A password manager does not provide any additional security for your passwords, and instead of doing the sensible thing and removing the risky element all together, continue to instill that password responsibility falls to the user.
Many use World Password Day to remind others of the value of password managers, but password managers should only be considered a solution for those who have trouble remembering passwords and are not concerned at all with security. If you are looking to improve security, they are not a viable solution.
The Benefits of Passwordless on World Password Day
While it feels helpful to share these password security recommendations on days like today, organizations need to make a concerted effort to make their authentication process more secure, rather than putting any unnecessary or undue pressure on the user. Following password recommendations will only give the individual user the illusion of being in control of their security, but if they are phished or there is a breach then adding more characters or using a password manager will be of no help. Keeping your customers, employees, and users secure is vital to building and maintaining trust within your organization.
Beyond Identity eliminates passwords entirely, leaving no credentials for malicious threat actors to breach or steal, either through a password manager, a database breach, or other malicious means. Beyond Identity verifies users and identities using the same cryptographic principles that TLS uses to secure trillions of dollars of transactions daily. It’s time that every organization remembers the one password tip that actually works… get rid of them!
Why are we still burdening users with the nearly impossible task of maintaining secure passwords?
Passwords are fundamentally flawed for a number of reasons—they are difficult to keep safe, long and arduous to remember, and easily susceptible to breach or attack. Many organizations use World Password Day as a way to offer up some helpful tips, like these, on how to keep a password secure…
- “Use at least 15 characters”
- “Mix up letters and symbols”
- “Don’t use sequential numbers”
- “Avoid using personal information”
And more, to put the onus on the user to keep their personal information secure. Organizations will prompt users to change or update their passwords to “enhance security” and offer up these tips or requirements. But why aren’t we demanding the organization itself to investigate other, more secure forms of authentication? Try as you might to secure passwords, but they will always lack the security that a passwordless solution can provide. Here’s why some of these tips, while likely well intended, make little difference in improving security.
Frequently Given Tips That Don’t Work
Some of the most commonly recommended tips when it comes to passwords can be some of the most useless. There are many ways in which passwords can easily be breached or hacked, resulting in huge problems for your organization, even if you follow all the “best practices” for passwords. For example, much of the advice you will come across on the internet reminds the user to use long, strong passwords, such as using a combination of symbols and letters, not reusing previous passwords, and not making your password easy to guess, such as “p@ssword”, but even following this advice will not keep your password safe.

A password is a “shared secret”, meaning it is a piece of information known by both the user and the service provider, and as a result of this are fundamentally insecure because of the risk of being breached on either end. Most organizations put this blame entirely on the user, forcing them to regularly change their passwords, extend the length, and create a poor experience.
If your credentials are password-based, then they are stored in databases, and this is a huge problem for the security of your applications and systems. Databases are breached with alarming frequency, and no organization is safe—even Microsoft. It doesn’t matter if your password is 2,213 characters long and chock full of symbols. When a user is tricked by a phishing email, the complexity of their password is irrelevant. As long as passwords are being used, they will be stolen, because of their existence in multiple places and ability to be stolen or breached.
Unlike shared secrets, passwordless authentication eliminates passwords all together, leaving no credentials for hackers to snatch in the first place. Organizations need to take responsibility for authentication security and make the move beyond passwords.
The False Security of Password Managers
Another common piece of advice is to use a password manager. A password manager is, in essence, a way to store and generate your login information in an encrypted way to access applications, websites, and systems. What many people don’t realize is that password managers carry the same problems that passwords do. The password still exists, it is just hidden from the user. This may make it more convenient for the user but not any more secure.
- All your sensitive information is in one place, so the potential for damage caused by a hack is frightening to consider
- Your password manager has a password of its own
- Your password is still a shared secret but now its shared with one more party (the password manager)
The password manager is a solution designed by a system that wants to pass responsibility off to the user for breaches by assigning the safety of a password to the user. A password manager does not provide any additional security for your passwords, and instead of doing the sensible thing and removing the risky element all together, continue to instill that password responsibility falls to the user.
Many use World Password Day to remind others of the value of password managers, but password managers should only be considered a solution for those who have trouble remembering passwords and are not concerned at all with security. If you are looking to improve security, they are not a viable solution.
The Benefits of Passwordless on World Password Day
While it feels helpful to share these password security recommendations on days like today, organizations need to make a concerted effort to make their authentication process more secure, rather than putting any unnecessary or undue pressure on the user. Following password recommendations will only give the individual user the illusion of being in control of their security, but if they are phished or there is a breach then adding more characters or using a password manager will be of no help. Keeping your customers, employees, and users secure is vital to building and maintaining trust within your organization.
Beyond Identity eliminates passwords entirely, leaving no credentials for malicious threat actors to breach or steal, either through a password manager, a database breach, or other malicious means. Beyond Identity verifies users and identities using the same cryptographic principles that TLS uses to secure trillions of dollars of transactions daily. It’s time that every organization remembers the one password tip that actually works… get rid of them!
Why are we still burdening users with the nearly impossible task of maintaining secure passwords?
Passwords are fundamentally flawed for a number of reasons—they are difficult to keep safe, long and arduous to remember, and easily susceptible to breach or attack. Many organizations use World Password Day as a way to offer up some helpful tips, like these, on how to keep a password secure…
- “Use at least 15 characters”
- “Mix up letters and symbols”
- “Don’t use sequential numbers”
- “Avoid using personal information”
And more, to put the onus on the user to keep their personal information secure. Organizations will prompt users to change or update their passwords to “enhance security” and offer up these tips or requirements. But why aren’t we demanding the organization itself to investigate other, more secure forms of authentication? Try as you might to secure passwords, but they will always lack the security that a passwordless solution can provide. Here’s why some of these tips, while likely well intended, make little difference in improving security.
Frequently Given Tips That Don’t Work
Some of the most commonly recommended tips when it comes to passwords can be some of the most useless. There are many ways in which passwords can easily be breached or hacked, resulting in huge problems for your organization, even if you follow all the “best practices” for passwords. For example, much of the advice you will come across on the internet reminds the user to use long, strong passwords, such as using a combination of symbols and letters, not reusing previous passwords, and not making your password easy to guess, such as “p@ssword”, but even following this advice will not keep your password safe.

A password is a “shared secret”, meaning it is a piece of information known by both the user and the service provider, and as a result of this are fundamentally insecure because of the risk of being breached on either end. Most organizations put this blame entirely on the user, forcing them to regularly change their passwords, extend the length, and create a poor experience.
If your credentials are password-based, then they are stored in databases, and this is a huge problem for the security of your applications and systems. Databases are breached with alarming frequency, and no organization is safe—even Microsoft. It doesn’t matter if your password is 2,213 characters long and chock full of symbols. When a user is tricked by a phishing email, the complexity of their password is irrelevant. As long as passwords are being used, they will be stolen, because of their existence in multiple places and ability to be stolen or breached.
Unlike shared secrets, passwordless authentication eliminates passwords all together, leaving no credentials for hackers to snatch in the first place. Organizations need to take responsibility for authentication security and make the move beyond passwords.
The False Security of Password Managers
Another common piece of advice is to use a password manager. A password manager is, in essence, a way to store and generate your login information in an encrypted way to access applications, websites, and systems. What many people don’t realize is that password managers carry the same problems that passwords do. The password still exists, it is just hidden from the user. This may make it more convenient for the user but not any more secure.
- All your sensitive information is in one place, so the potential for damage caused by a hack is frightening to consider
- Your password manager has a password of its own
- Your password is still a shared secret but now its shared with one more party (the password manager)
The password manager is a solution designed by a system that wants to pass responsibility off to the user for breaches by assigning the safety of a password to the user. A password manager does not provide any additional security for your passwords, and instead of doing the sensible thing and removing the risky element all together, continue to instill that password responsibility falls to the user.
Many use World Password Day to remind others of the value of password managers, but password managers should only be considered a solution for those who have trouble remembering passwords and are not concerned at all with security. If you are looking to improve security, they are not a viable solution.
The Benefits of Passwordless on World Password Day
While it feels helpful to share these password security recommendations on days like today, organizations need to make a concerted effort to make their authentication process more secure, rather than putting any unnecessary or undue pressure on the user. Following password recommendations will only give the individual user the illusion of being in control of their security, but if they are phished or there is a breach then adding more characters or using a password manager will be of no help. Keeping your customers, employees, and users secure is vital to building and maintaining trust within your organization.
Beyond Identity eliminates passwords entirely, leaving no credentials for malicious threat actors to breach or steal, either through a password manager, a database breach, or other malicious means. Beyond Identity verifies users and identities using the same cryptographic principles that TLS uses to secure trillions of dollars of transactions daily. It’s time that every organization remembers the one password tip that actually works… get rid of them!








.jpg)
.jpg)
.jpg)

.jpg)
.jpg)



.jpeg)






.png)

