ChatGPT's Dark Side: Cyber Experts Warn AI Will Aid Cyberattacks in 2023
Key takeaways
- More than one in six cybersecurity specialists had worked for companies that experienced an AI-fueled cyberattack.
- 75% of cybersecurity specialists say that AI use in cyberattacks is on the rise.
- Handling a lot of data is the top benefit of using AI in cybersecurity, according to 58% of specialists.
- Over 50% of cybersecurity specialists consider identifying spam and phishing emails as one of the key advantages of using AI in cybersecurity.
The role of AI in cybersecurity
As technology becomes increasingly integrated into our daily lives, cybersecurity threats become more of a concern as well. And as AI evolves, so does its potential to assist in cyberattacks. For an in-depth look at AI-assisted cyberattacks, we asked cybersecurity experts what they’re like, what the consequences are, and how to prevent and overcome them. They also shared the pros and cons of using AI in cybersecurity overall. Their answers can help you stay on the cutting edge of cybersecurity.
The age of AI-powered cybercrime
Cybercriminals are using AI, but are they using it for more than phishing? This first part of our research has the answer and also reveals the consequences.
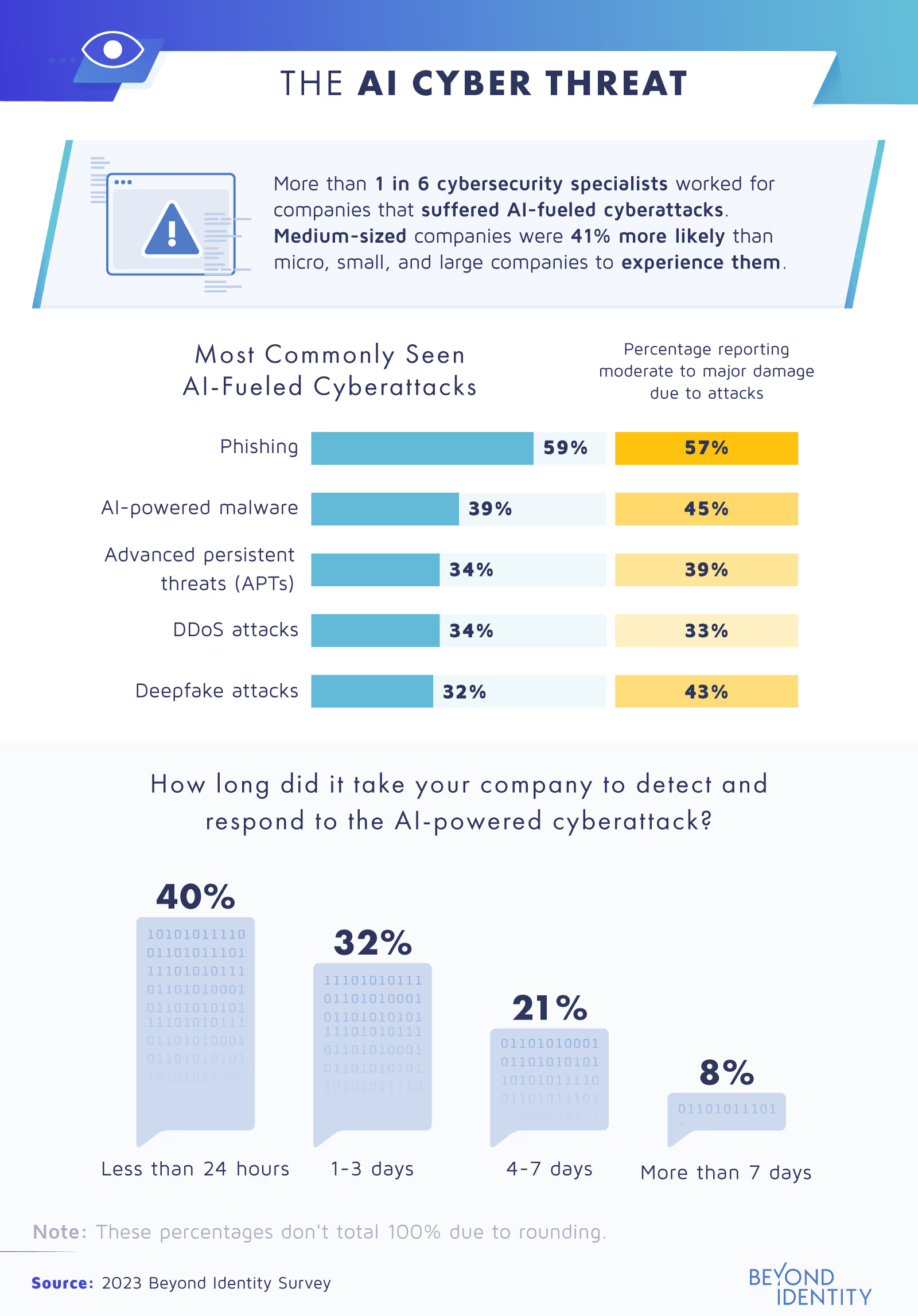
More than one in six cybersecurity experts we surveyed said they’d worked for a company that fell victim to an AI-assisted cyberattack. Most of the time, it involved phishing, which resulted in moderate to major damage 57% of the time. This means the company lost some data or assets, suffered a significant financial loss, or experienced a long-term service disruption.
Fortunately, 40% of respondents said it took less than 24 hours to detect the attack and respond accordingly. But that doesn’t mean they were able to recover their losses. A cyber insurance plan can help cover the costs of a breach, preventing a hard blow like this from affecting a company’s bottom line.
The growing threat of AI cyberattacks
Cybersecurity specialists also weighed in on just how much of a threat certain AI platforms are and why.
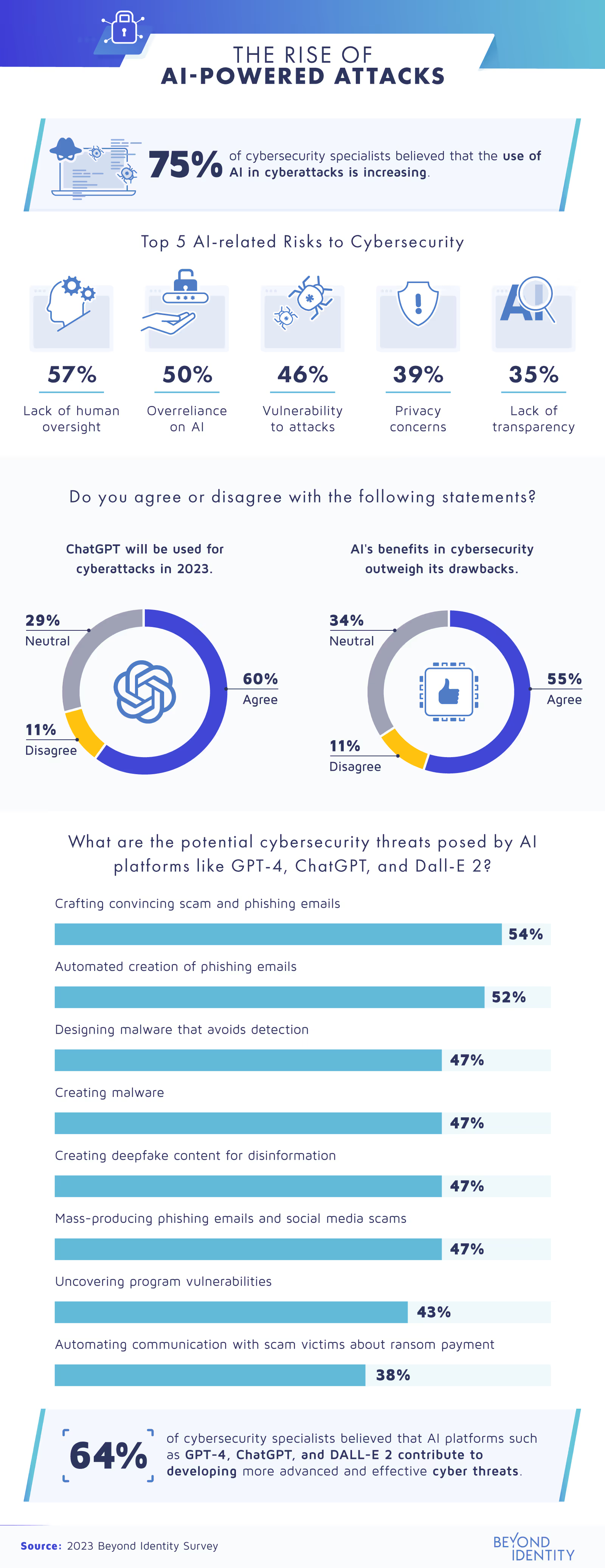
Three-quarters of the professionals we surveyed felt that AI use in cyberattacks is increasing. Most (64%) specifically said platforms like GPT-4, ChatGPT, and DALL-E 2 allow cybercriminals to develop more advanced and effective tactics. The most commonly named risks of AI-powered cybersecurity were:
- Reduced human oversight
- Relying too heavily on AI
- Increased vulnerability to cyberattacks
- Data privacy issues
- Lack of transparency
The top cybersecurity threats these specialists pointed to involved using AI for writing and coding tasks. AI tools like ChatGPT can automatically write emails, including those used in phishing scams. Others can write code, making it easier for cybercriminals to design undetectable malware.
But despite our respondents’ concerns, more than half also expressed that AI provides more cybersecurity benefits than risks. We’ll expand on that next.
AI’s cybersecurity advantages
Now that we’ve discussed how AI can help cybercriminals, let’s see how it can give your cybersecurity the edge it needs to prevent attacks.
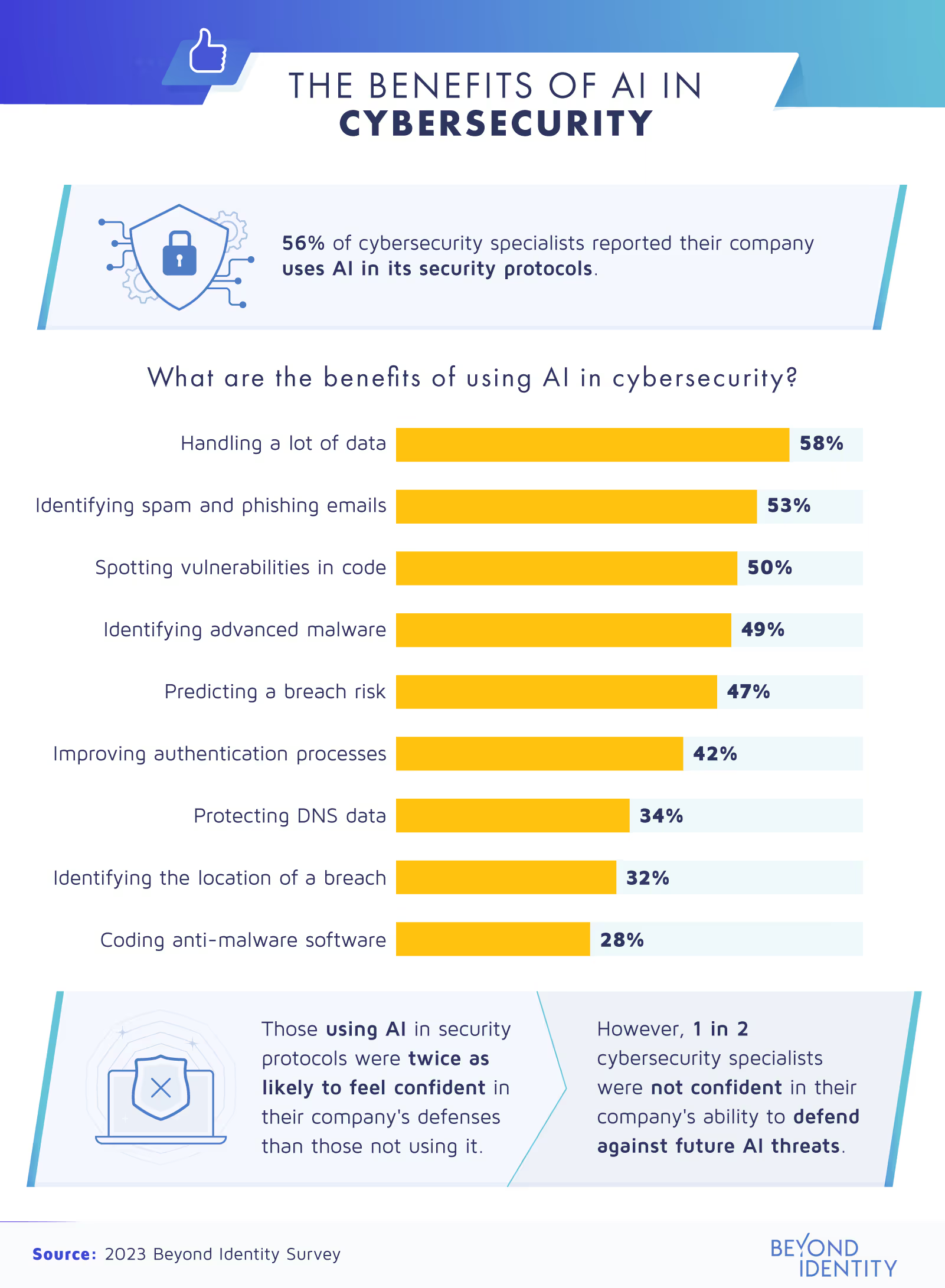
According to the experts surveyed, the top cybersecurity benefit AI has offered them is handling large amounts of data (58%). More than half also shared that AI is a great tool for identifying spam emails and phishing attempts. This illustrates how AI can pose just as much of a cybersecurity advantage as it does a threat.
So, it’s no surprise that more than half of our respondents worked for a company that utilized AI as part of their cybersecurity protocol. For a closer look, here are the percentages of those working in each industry who gave this response:
- Tech: 64%
- Finance: 63%
- Marketing: 60%
- Health care: 55%
- Retail: 54%
The likelihood of someone’s company using AI for cybersecurity also varied by company size:
- Micro: 37%
- Small: 60%
- Medium: 62%
- Large: 55%
Since smaller businesses have smaller budgets, they’re likely among those that take a bigger hit from any losses they experience due to cybercrime. They’re also more likely to have fewer people, and thus less time and labor to dedicate to cybersecurity. AI can fill in the gaps when a human touch isn’t possible, and you’re about to learn exactly how.
Proactive approaches
Now, let’s see what advice cybersecurity professionals had to offer for using AI to protect business data and assets.
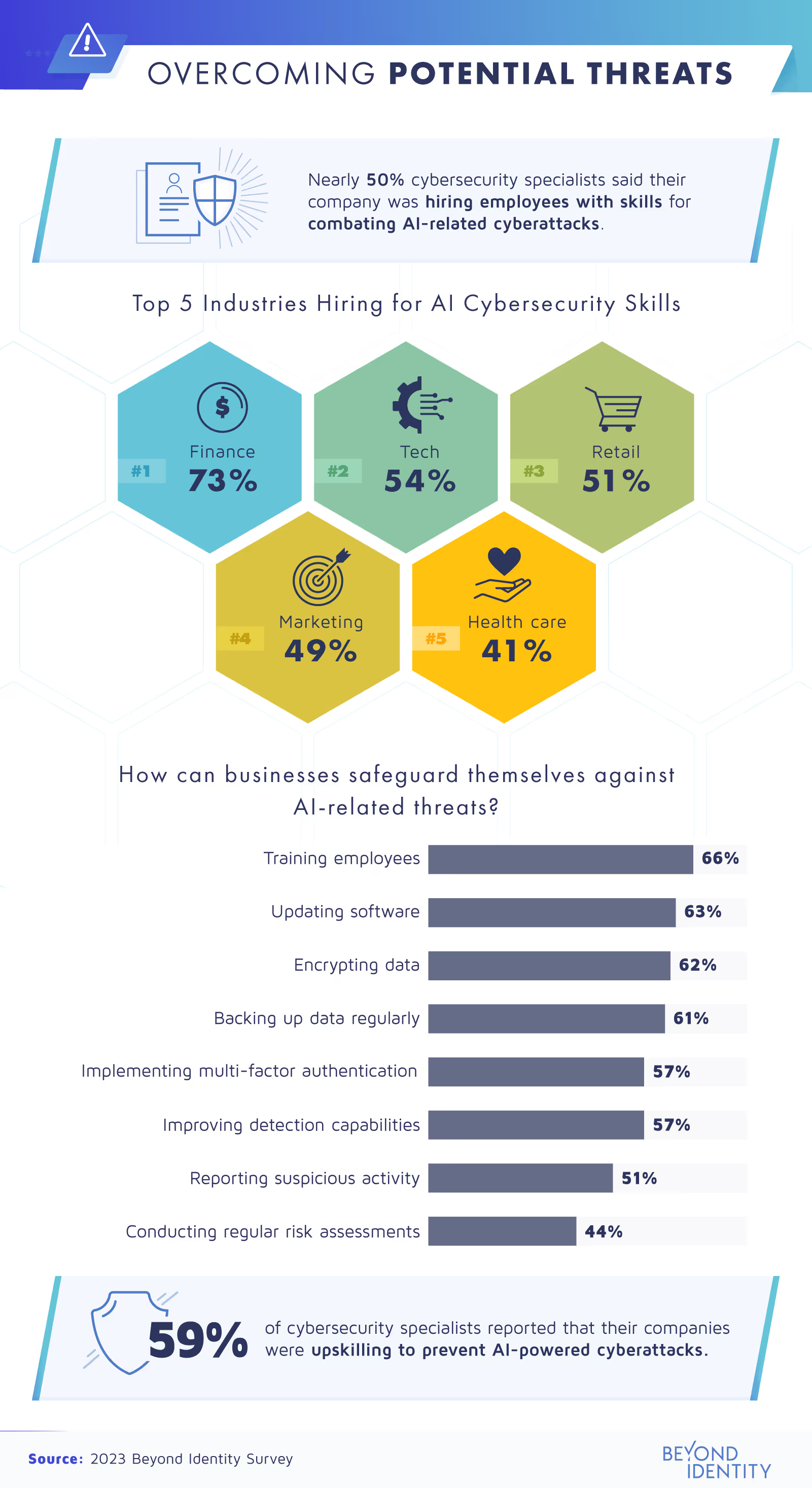
Since we’ve learned that the lack of human oversight is one of the top risks of AI-assisted cybersecurity, it makes sense that most specialists’ top tip for mitigating this threat was training employees (66%). This is especially important for remote teams, which are more vulnerable to cyberattacks.
Here are some key tips from the cybersecurity experts who participated in our study:
- Invest in AI research and development
- Develop AI-specific cybersecurity measures
- Educate employees on current AI threats
- Regularly perform cybersecurity audits
Embracing the Power of AI
Although most cybersecurity professionals understand that AI poses a new threat to cybersecurity, they also weigh the threat against AI’s benefits for safeguarding their companies’ data and assets. The best ways to prevent AI-powered cyberattacks involve vigilance and proper communication within your organization. And it doesn’t hurt to fight fire with fire and employ the benefits of AI in your cybersecurity protocols just as cybercriminals do in their tactics—just make sure you maintain human oversight.
Methodology
For this campaign, we surveyed 1,010 cybersecurity specialists. Among them, 67% were men, 32% were women, and 1% preferred not to say. Of them, 20% had up to three years of experience, 57% had three to six years, and 23% had seven or more years.
About Beyond Identity
Beyond Identity offers phishing-resistant MFA and passwordless MFA, which provides frictionless security users will readily adopt. Our Zero Trust Authentication solution lets you set the foundation for zero trust by assessing device risk on a continuous basis so you can truly protect your data.
Fair use statement
If you’d like to share these cybersecurity tips for any non-commercial purpose, please feel free to do so. We only ask that you include a link to this page to credit our research team.













.avif)
.avif)



.avif)






.avif)

