Hacking Microsoft in Real Time: Number Matching
Transcript
In this video, we will see how traditional 2FA fails to prevent a phishing attack. Our demo begins with our threat actor, Clara, responding to a victim, Stanley. Stanley has enabled Microsoft push notifications with number matching in an attempt to prevent a phishing attack.
Clara embeds a phishing link in her email and sends it off. Now, Clara will wait until the victim opens the email.
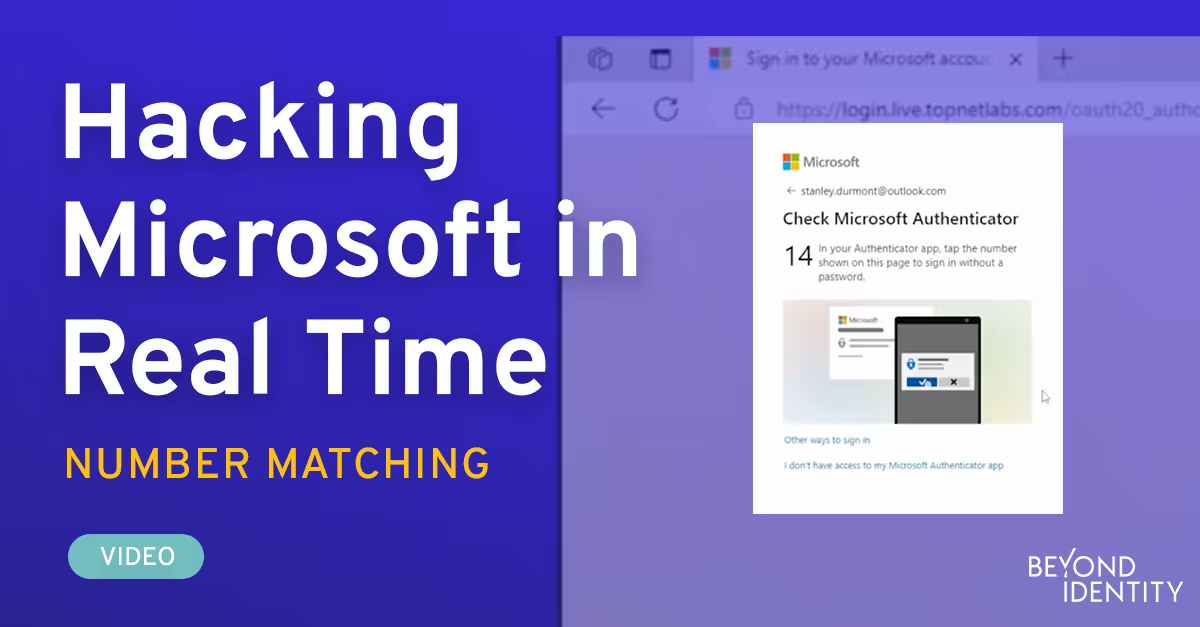
Stanley, working on payroll, receives a reply from Clara. He clicks the link and logs in. At this point, Microsoft will ask him to use his Authenticator application. It's a push notification asking him to select the number 14. Over on his iPad, he unlocks the screen and selects the number 14 in response to the push notification.
The webpage gets a notification that Stanley selected the right number and logs him in. However, Stanley finds no shared files since they don't exist.
As soon as Stanley opened the link, Clara began to see traffic in her phishing proxy. At this point, Clara can see some polling behavior. This is how the webpage checks with the server to see when the user has completed the push notification task.
Clara waits for a while until she sees that Stanley submitted the form and completed the login process. Once Clara sees that all authorization tokens have been intercepted, she interacts with the proxy in order to dump the session. Here, there was no password in use, so no password was captured. However, the proxy still captured the cookie that the server granted to Stanley's web browser.
Clara takes this cookie and with the help of a Chrome extension, she executes a session takeover, gaining access to Stanley's account. Now that Clara has a foothold into Stanley's account, she can act as Stanley, access his documents, and escalate her attack.
Transcript
In this video, we will see how traditional 2FA fails to prevent a phishing attack. Our demo begins with our threat actor, Clara, responding to a victim, Stanley. Stanley has enabled Microsoft push notifications with number matching in an attempt to prevent a phishing attack.
Clara embeds a phishing link in her email and sends it off. Now, Clara will wait until the victim opens the email.
Stanley, working on payroll, receives a reply from Clara. He clicks the link and logs in. At this point, Microsoft will ask him to use his Authenticator application. It's a push notification asking him to select the number 14. Over on his iPad, he unlocks the screen and selects the number 14 in response to the push notification.
The webpage gets a notification that Stanley selected the right number and logs him in. However, Stanley finds no shared files since they don't exist.
As soon as Stanley opened the link, Clara began to see traffic in her phishing proxy. At this point, Clara can see some polling behavior. This is how the webpage checks with the server to see when the user has completed the push notification task.
Clara waits for a while until she sees that Stanley submitted the form and completed the login process. Once Clara sees that all authorization tokens have been intercepted, she interacts with the proxy in order to dump the session. Here, there was no password in use, so no password was captured. However, the proxy still captured the cookie that the server granted to Stanley's web browser.
Clara takes this cookie and with the help of a Chrome extension, she executes a session takeover, gaining access to Stanley's account. Now that Clara has a foothold into Stanley's account, she can act as Stanley, access his documents, and escalate her attack.
Transcript
In this video, we will see how traditional 2FA fails to prevent a phishing attack. Our demo begins with our threat actor, Clara, responding to a victim, Stanley. Stanley has enabled Microsoft push notifications with number matching in an attempt to prevent a phishing attack.
Clara embeds a phishing link in her email and sends it off. Now, Clara will wait until the victim opens the email.
Stanley, working on payroll, receives a reply from Clara. He clicks the link and logs in. At this point, Microsoft will ask him to use his Authenticator application. It's a push notification asking him to select the number 14. Over on his iPad, he unlocks the screen and selects the number 14 in response to the push notification.
The webpage gets a notification that Stanley selected the right number and logs him in. However, Stanley finds no shared files since they don't exist.
As soon as Stanley opened the link, Clara began to see traffic in her phishing proxy. At this point, Clara can see some polling behavior. This is how the webpage checks with the server to see when the user has completed the push notification task.
Clara waits for a while until she sees that Stanley submitted the form and completed the login process. Once Clara sees that all authorization tokens have been intercepted, she interacts with the proxy in order to dump the session. Here, there was no password in use, so no password was captured. However, the proxy still captured the cookie that the server granted to Stanley's web browser.
Clara takes this cookie and with the help of a Chrome extension, she executes a session takeover, gaining access to Stanley's account. Now that Clara has a foothold into Stanley's account, she can act as Stanley, access his documents, and escalate her attack.









.avif)
.avif)
.avif)

.avif)



.avif)






.avif)

