Guarding the Gates: Navigating Okta's Confusing Recommendations for a Robust Security Posture
Over the past decade, the deployment of Single Sign-On (SSO) solutions like Okta has become commonplace, heralding a new era of convenience and efficiency in managing workforce identities and applications. However, the journey toward securing these systems is fraught with complexities, often exacerbated by conflicting and sometimes confusing recommendations within Okta's own guidebooks. For well-intentioned administrators, navigating these waters can be perilous, with the risk of unknowingly making security sacrifices that could have devastating consequences for their organizations.
To navigate these challenges, we dissect three specific recommendations from Okta's publications that endorse practices potentially weakening your security posture. Our goal is to arm you with the insights needed to identify and rectify vulnerabilities within your SSO environment, as well as provide the tools for tailored recommendations.
Recommendation 1: High Assurance Level Authenticators and FastPass
Recommendation 2: phishing-resistant authentication as a delayed priority
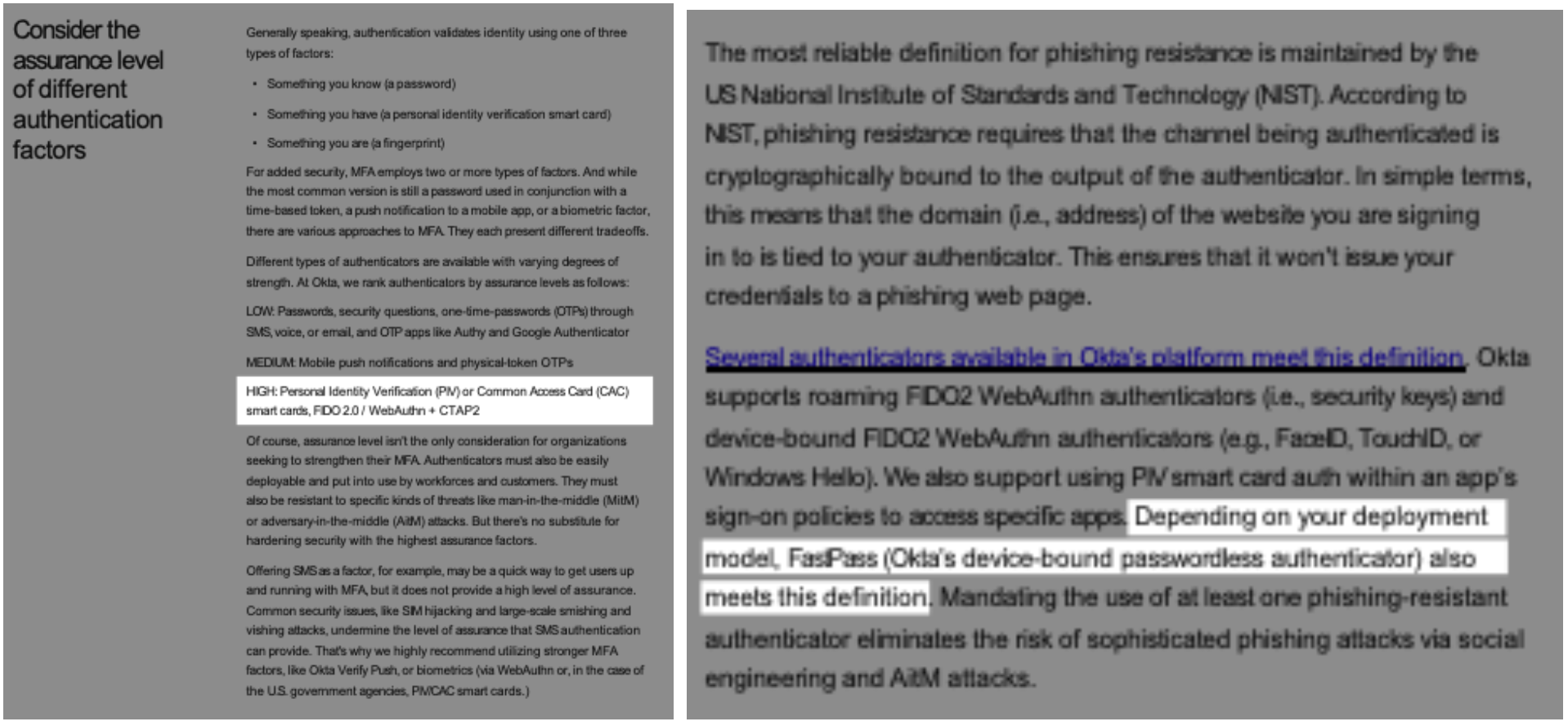
Okta's "Multi-Factor Authentication Deployment Guide" lauds the security of PIV/CAC smart cards, FIDO2 security tokens, and WebAuthn as high assurance level authenticators. Yet, it ambiguously classifies FastPass, Okta’s device-bound passwordless authenticator, as fitting this high assurance category "depending on your deployment model." This vague disclaimer introduces ambiguity that could lead organizations to adopt FastPass without fully understanding its limitations or the specific deployment contexts in which it provides comparable security levels. Organizations should demand clarity and unequivocally adopt genuinely high assurance level authenticators, ensuring no room for ambiguity that could compromise security.
In "A Comprehensive Guide for Your Workforce Identity Maturity Journey," Okta suggests introducing phishing-resistant authentications at Stage 3 of the identity maturity model, despite earlier stages proposing solutions like Adaptive MFA to enhance phishing resistance. This staggered approach could inadvertently lower the security threshold, exposing organizations to phishing risks earlier in their Okta journey. From the outset, organizations should prioritize phishing-resistant authentication methods, sidestepping insecure practices that compromise the integrity of their digital environment due to perceived inconvenience or compatibility issues.
Recommendation 3: The ambiguous positioning of FastPass

The "Step-by-step guide to becoming phishing resistant with Okta FastPass" offers a convoluted stance on implementing FastPass, advising against a global "Sign in with FastPass" setting. Instead, it recommends controlling its display down to specific users and applications. This approach attempts to normalize the coexistence of phishing-resistant authentication with less secure methods, undermining the overall security framework. True security is compromised by the weakest link; hence, advocating for a mixed authentication environment dilutes the effectiveness of phishing-resistant measures. Organizations should advocate for consistent, strong authentication experiences across the board, rejecting half-measures that leave them vulnerable.
What your organization can do today
Understanding and addressing these concerns is crucial for administrators tasked with safeguarding their SSO environments. The nuanced vulnerabilities and the potential for misinterpretation of Okta's recommendations necessitate a vigilant, informed approach to configuring these systems.
For those looking to assess the security posture of their Okta configurations and identify potential misconfigurations, Access360 offers a pragmatic solution. This tool provides an instant report analyzing your Okta environment, delivering actionable insights and recommendations to enhance the security of your SSO setup.
Over the past decade, the deployment of Single Sign-On (SSO) solutions like Okta has become commonplace, heralding a new era of convenience and efficiency in managing workforce identities and applications. However, the journey toward securing these systems is fraught with complexities, often exacerbated by conflicting and sometimes confusing recommendations within Okta's own guidebooks. For well-intentioned administrators, navigating these waters can be perilous, with the risk of unknowingly making security sacrifices that could have devastating consequences for their organizations.
To navigate these challenges, we dissect three specific recommendations from Okta's publications that endorse practices potentially weakening your security posture. Our goal is to arm you with the insights needed to identify and rectify vulnerabilities within your SSO environment, as well as provide the tools for tailored recommendations.
Recommendation 1: High Assurance Level Authenticators and FastPass

Recommendation 2: phishing-resistant authentication as a delayed priority
Okta's "Multi-Factor Authentication Deployment Guide" lauds the security of PIV/CAC smart cards, FIDO2 security tokens, and WebAuthn as high assurance level authenticators. Yet, it ambiguously classifies FastPass, Okta’s device-bound passwordless authenticator, as fitting this high assurance category "depending on your deployment model." This vague disclaimer introduces ambiguity that could lead organizations to adopt FastPass without fully understanding its limitations or the specific deployment contexts in which it provides comparable security levels. Organizations should demand clarity and unequivocally adopt genuinely high assurance level authenticators, ensuring no room for ambiguity that could compromise security.
In "A Comprehensive Guide for Your Workforce Identity Maturity Journey," Okta suggests introducing phishing-resistant authentications at Stage 3 of the identity maturity model, despite earlier stages proposing solutions like Adaptive MFA to enhance phishing resistance. This staggered approach could inadvertently lower the security threshold, exposing organizations to phishing risks earlier in their Okta journey. From the outset, organizations should prioritize phishing-resistant authentication methods, sidestepping insecure practices that compromise the integrity of their digital environment due to perceived inconvenience or compatibility issues.
Recommendation 3: The ambiguous positioning of FastPass

The "Step-by-step guide to becoming phishing resistant with Okta FastPass" offers a convoluted stance on implementing FastPass, advising against a global "Sign in with FastPass" setting. Instead, it recommends controlling its display down to specific users and applications. This approach attempts to normalize the coexistence of phishing-resistant authentication with less secure methods, undermining the overall security framework. True security is compromised by the weakest link; hence, advocating for a mixed authentication environment dilutes the effectiveness of phishing-resistant measures. Organizations should advocate for consistent, strong authentication experiences across the board, rejecting half-measures that leave them vulnerable.
What your organization can do today
Understanding and addressing these concerns is crucial for administrators tasked with safeguarding their SSO environments. The nuanced vulnerabilities and the potential for misinterpretation of Okta's recommendations necessitate a vigilant, informed approach to configuring these systems.
For those looking to assess the security posture of their Okta configurations and identify potential misconfigurations, Access360 offers a pragmatic solution. This tool provides an instant report analyzing your Okta environment, delivering actionable insights and recommendations to enhance the security of your SSO setup.
Over the past decade, the deployment of Single Sign-On (SSO) solutions like Okta has become commonplace, heralding a new era of convenience and efficiency in managing workforce identities and applications. However, the journey toward securing these systems is fraught with complexities, often exacerbated by conflicting and sometimes confusing recommendations within Okta's own guidebooks. For well-intentioned administrators, navigating these waters can be perilous, with the risk of unknowingly making security sacrifices that could have devastating consequences for their organizations.
To navigate these challenges, we dissect three specific recommendations from Okta's publications that endorse practices potentially weakening your security posture. Our goal is to arm you with the insights needed to identify and rectify vulnerabilities within your SSO environment, as well as provide the tools for tailored recommendations.
Recommendation 1: High Assurance Level Authenticators and FastPass

Recommendation 2: phishing-resistant authentication as a delayed priority
Okta's "Multi-Factor Authentication Deployment Guide" lauds the security of PIV/CAC smart cards, FIDO2 security tokens, and WebAuthn as high assurance level authenticators. Yet, it ambiguously classifies FastPass, Okta’s device-bound passwordless authenticator, as fitting this high assurance category "depending on your deployment model." This vague disclaimer introduces ambiguity that could lead organizations to adopt FastPass without fully understanding its limitations or the specific deployment contexts in which it provides comparable security levels. Organizations should demand clarity and unequivocally adopt genuinely high assurance level authenticators, ensuring no room for ambiguity that could compromise security.
In "A Comprehensive Guide for Your Workforce Identity Maturity Journey," Okta suggests introducing phishing-resistant authentications at Stage 3 of the identity maturity model, despite earlier stages proposing solutions like Adaptive MFA to enhance phishing resistance. This staggered approach could inadvertently lower the security threshold, exposing organizations to phishing risks earlier in their Okta journey. From the outset, organizations should prioritize phishing-resistant authentication methods, sidestepping insecure practices that compromise the integrity of their digital environment due to perceived inconvenience or compatibility issues.
Recommendation 3: The ambiguous positioning of FastPass

The "Step-by-step guide to becoming phishing resistant with Okta FastPass" offers a convoluted stance on implementing FastPass, advising against a global "Sign in with FastPass" setting. Instead, it recommends controlling its display down to specific users and applications. This approach attempts to normalize the coexistence of phishing-resistant authentication with less secure methods, undermining the overall security framework. True security is compromised by the weakest link; hence, advocating for a mixed authentication environment dilutes the effectiveness of phishing-resistant measures. Organizations should advocate for consistent, strong authentication experiences across the board, rejecting half-measures that leave them vulnerable.
What your organization can do today
Understanding and addressing these concerns is crucial for administrators tasked with safeguarding their SSO environments. The nuanced vulnerabilities and the potential for misinterpretation of Okta's recommendations necessitate a vigilant, informed approach to configuring these systems.
For those looking to assess the security posture of their Okta configurations and identify potential misconfigurations, Access360 offers a pragmatic solution. This tool provides an instant report analyzing your Okta environment, delivering actionable insights and recommendations to enhance the security of your SSO setup.







.jpg)
.jpg)
.jpg)

.jpg)
.jpg)
.jpg)
.jpg)



.jpeg)






.png)

