Device-Agnostic Security
Secure access for managed & unmanaged devices
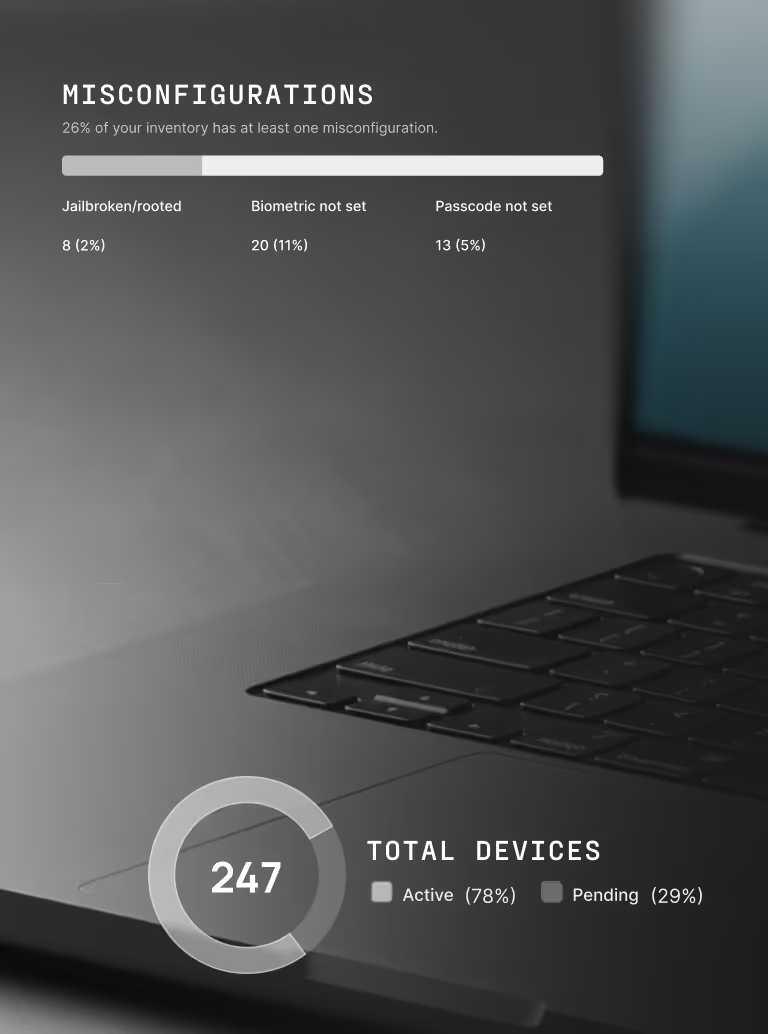
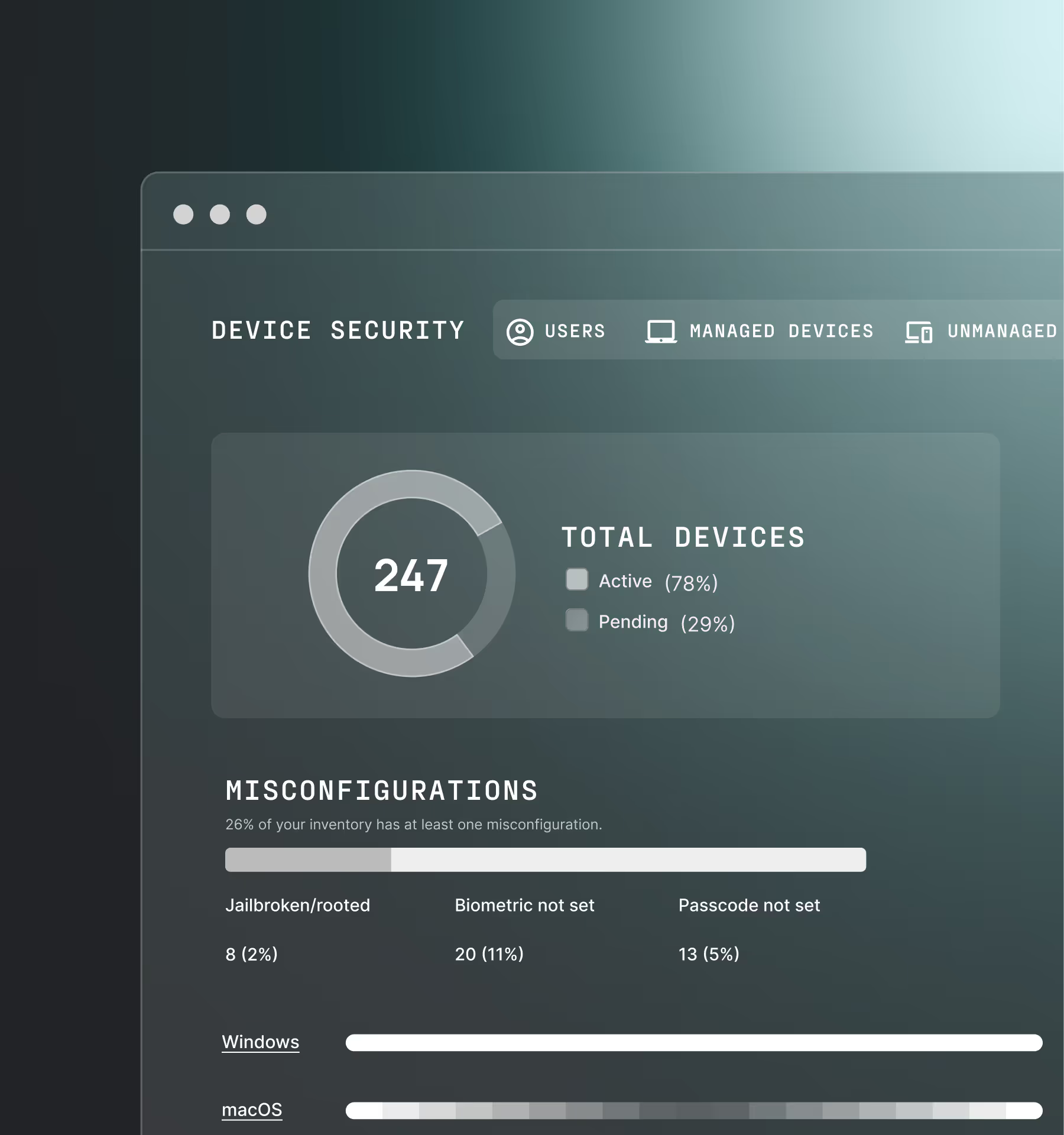
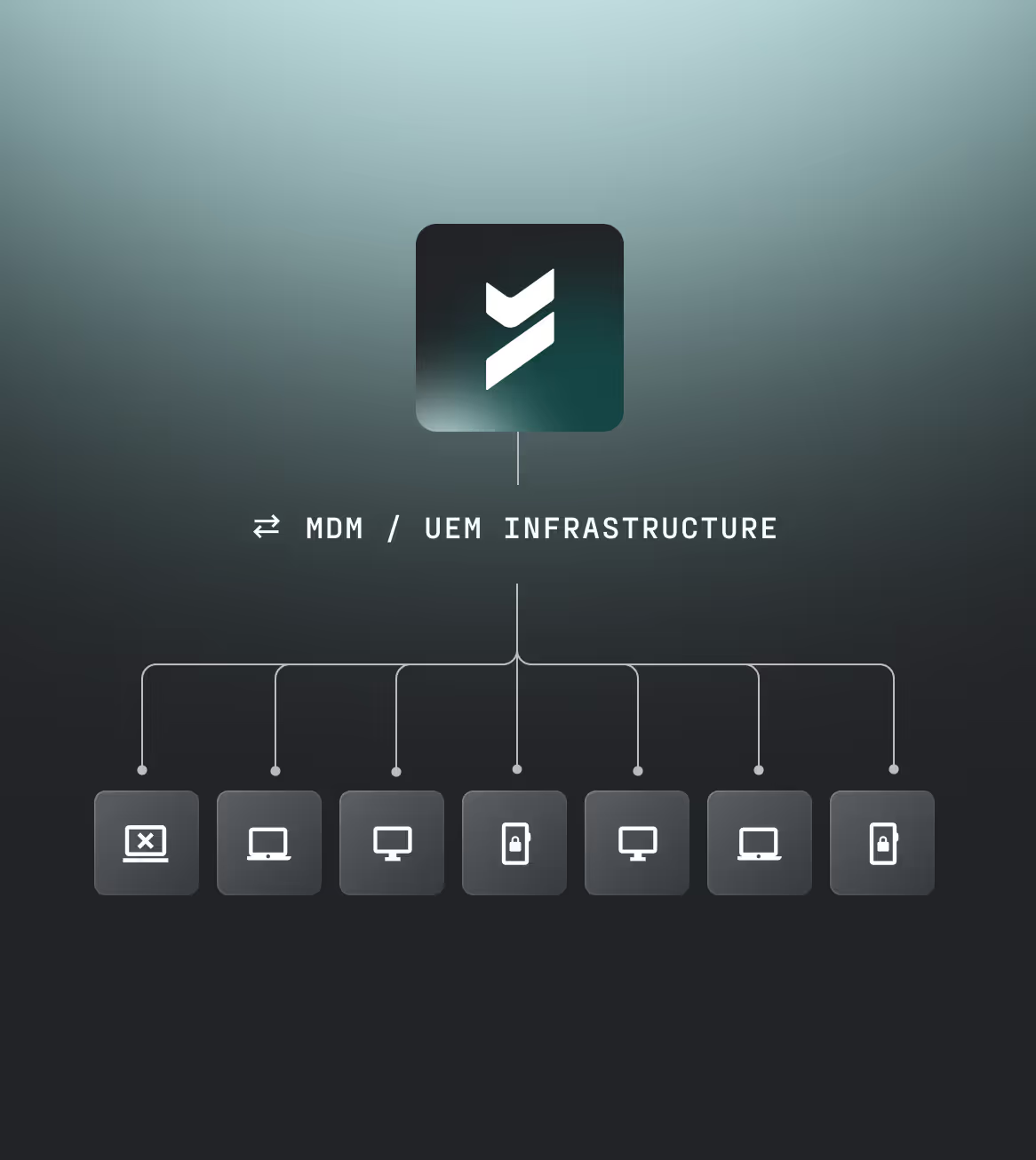
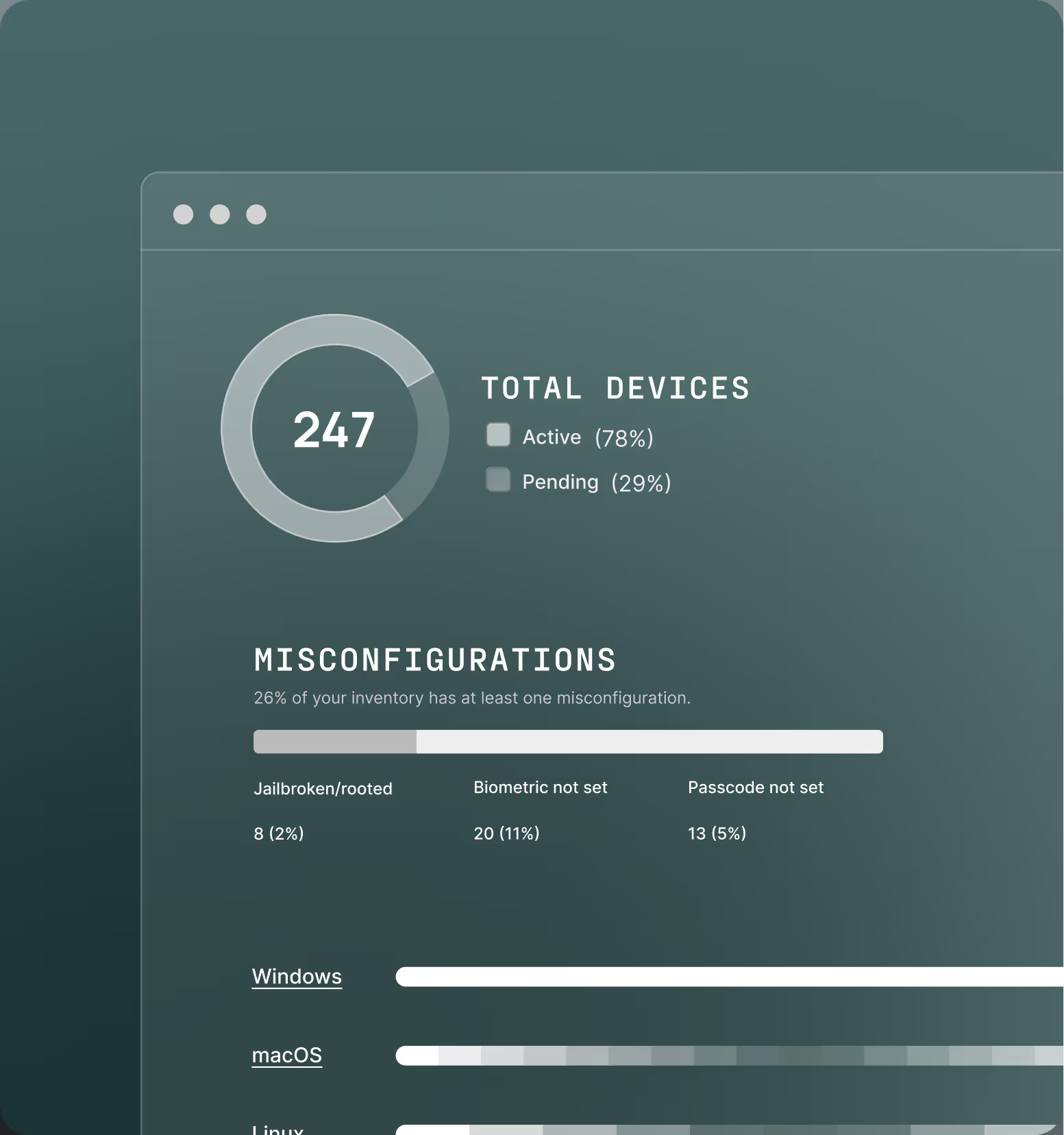
Secure entire device fleet
Authenticate continuously
Enforce access controls
.avif)
Modern devices, modern risks
MDMs and EDRs are invasive
Contractors and users resist adoption, leaving devices with no visibility
Session cookies leak access
Exposed in major breaches like Okta (2023)
2FA relies on second devices
Adds friction and expands the attack surface
Legacy MFA is insecure
Easily phished, replayed, or bypassed
46%
of the systems compromised with an infostealer that had possible corporate login data were non-managed devices. (Verizon, 2025)
The solution
Device security, across your entire fleet
Protect corporate resources accessed by BYOD, contractors, and unmanaged endpoints, regardless of what OS they use.
Built-in device trust.
No extra steps.
Our products verify the device before access is granted — automatically. From login and throughout the workday, we continuously check that devices meet your security standards, without slowing users down.


.avif)
.avif)
.avif)
.avif)

.png)

.png)
.jpg)
.png)


.jpg)

.jpg)



.jpg)

.jpg)


