Traditional Two-Factor Authentication vs. Beyond Identity’s Passwordless Authentication
Traditional Two-Factor or Multi-Factor Authentication (2FA/MFA) remains the “default” for dealing with fundamentally insecure, password-based authentication methods. We understand why they were the “go-to,” but hope to interrupt the “passwords are bad, so we need 2FA/MFA” refrain.
There is now a new option grabbing attention and gaining traction – Modern Passwordless Authentication. For our take on why the status quo needs to change, you can explore our blog: Is it finally time to kill traditional 2FA and MFA? We also discuss the ways traditional 2FA/MFA is vulnerable and provide examples in our blog: How Your MFA Can Be Hacked.
Let’s compare traditional 2FA/MFA against Beyond Identity’s Passwordless Authentication. We will take a look at them side-by-side across a few essential categories, including security, user experience, and compliance. These categories reflect the challenges shared between InfoSec teams and the account holders to ensure secure access, providing a good user experience, enabling rapid adoption.
Security
Traditional 2FA/MFA
Traditional 2FA/MFA solutions typically rely on a password as the first factor. Unfortunately, the second factor is often quite vulnerable.
Mobile device verification, using voice or text, is susceptible to SIM swaps, where a hacker tricks your carrier into switching over your phone line. These attacks are becoming increasingly common.
The one-time passwords (OTP) generated through 2FA/MFA can be hijacked and used by attackers who have access to a user’s email or SMS. These “one-time codes,” like passwords, are shared secrets that can be stolen and reused. OTPs can also be predicted by clever hackers. NIST has retracted its support for SMS-based MFA, and in November 2020, Microsoft urged users to stop using call & SMS-based multi-factor authentication.
Even the more secure 2FA/MFA approaches like push notifications, which use out-of-band channels, have their issues. Attackers now send multiple push notifications knowing that users, conditioned to clear them, will often approve them without thinking about the consequences – letting a bad guy in.
The second factor in traditional 2FA/MFAs merely inconvenience hackers but don’t do much to stop them.
Check out How Your MFA Can Be Hacked (With Examples) for a deeper dive into some of how traditional 2FA/MFA is vulnerable to attack.
Beyond Identity’s Passwordless Authentication
Our passwordless authentication fully eliminates the password. It does not hide the password behind another factor. Thus, there are no password databases for attackers to steal, and logins don’t rely on shared secrets of any kind. This approach stops credential stuffing, rainbow table attacks, and other password-based attacks in their tracks.
The most secure solutions rely on asymmetric cryptography for fundamentally secure authentication, rather than “symmetric,” shared secrets, like passwords, which are fundamentally insecure because they must be stored and known by both parties.
Beyond Identity uses a private key securely stored in a secure enclave or trusted platform module (TPM) on modern endpoint devices. The TPM signs a certificate with the private key that can be validated using the corresponding public key. The public key can be shared without any risk. We trust this model inherently and use the technology every day. TLS, the “lock in the browser,” ensures private data we exchange with servers remains private and secure. TLS employs X.509 certificates that are based on asymmetric cryptography and public-private key pairs.
Security is improved because there are no vulnerable passwords to steal, and the TPM housing the private key is not easily breached. According to a high-profile case from last January, even the U.S. Federal Bureau of Investigations has been unable to gain access to devices in their custody. These devices rely on TPM/enclaves and asymmetric crypto. Beyond Identity’s Modern Passwordless Authentication leverages X.509 certificates without the need for a certificate authority or any certificate management. It merely extends the Chain of Trust™ established by TLS to users and their devices.
Check out A Tale of Two Keys: The Simple Explanation of Passwordless for more of an explanation on asymmetric cryptography and how it’s used in passwordless authentication.
User Experience
Traditional 2FA/MFA
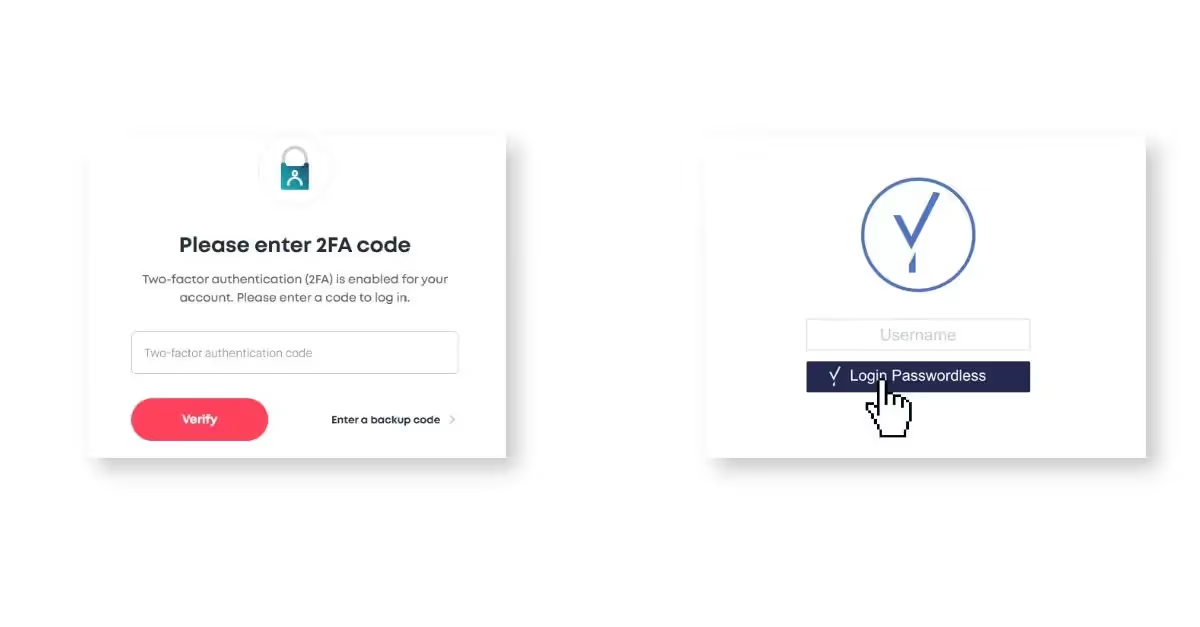
Barely half of Americans had bothered to set up traditional 2FA/MFA for even one account by the end of 2019, according to this article published by Dark Reading. Traditional 2FA/MFA is challenging to set up and adds friction to every login. First, users have to enter the password. Then they will have to access a second account, an app, or find their phone to verify themselves and complete the process.
In many consumer or workforce use cases, this means logging in to an email account or accessing the SMS on their mobile device. With one-time passwords (OTP) and “push notifications” – where an out-of-band signal is sent to an app on a mobile device and the user has to press the button to continue the login – the user will also have to locate and unlock their second device with each login. This traditional 2FA/MFA process, which is only incrementally more secure than a regular password login, creates significant and unwelcome inconvenience for end users.
Beyond Identity’s Passwordless Authentication
Modern passwordless authentication uses a new type of authenticator on the device to confirm user identity securely. The approach leverages the secure biometric (face or fingerprint) recognition technology built into modern endpoints.
This approach employs two authentication factors, something you are (biometric) and something you possess, the PC or mobile device you are logging in with. This form of multi-factor authentication is fundamentally secure. It provides a frictionless user experience since it does not require the user to pick up a second device or fish a code out of an SMS or email. Users love not having to memorize different passwords or change them periodically. Modern passwordless authentication provides extra security without the hassle of traditional 2FA/MFA.
Regulatory Compliance
Traditional 2FA/MFA
MFA has become the “go-to” option in many industries, but it’s typically not mandated in regulations. Most regulations (HIPAA and PCI, for example) simply require strong authentication. However, between regulators and auditor interpretation, traditional 2FA/MFA became a de facto standard. It was the only game in town and an easy-to-grasp concept when governments and industries were demanding more comprehensive authentication.
2FA/MFA got a boost a little over 15 years ago, when organizations such as the Federal Financial Institutions Examination Council (FFIEC) decried single-factor authentication as inadequate. They mentioned 2FA/MFA by name as a better alternative.
Beyond Identity’s Passwordless Authentication
Modern passwordless authentication solutions significantly improve security by removing weak factors (shared secrets) and leveraging multiple authentication factors so that auditors are completely satisfied. But these solutions can do this without frustrating end users and adversely impacting productivity. Organizations are deploying our passwordless authentication solution today because it passes auditor muster, and even Gartner® agrees that it is a robust alternative.
The Verdict
Providing strong authentication is an ongoing challenge that must balance comprehensive security against user experience. Traditional 2FA/MFA was a reasonable, if flawed, alternative for greater security in its day, but today the winner is clear. Beyond Identity’s Passwordless Authentication provides both a great user experience and a very high level of protection.
Explore Beyond Identity’s advanced Passwordless Identity Management Platform and learn how to provide a seamless, passwordless, multi-factor experience for both your workforce and customers. Also, explore Beyond Identity's passwordless MFA solution.
Traditional Two-Factor or Multi-Factor Authentication (2FA/MFA) remains the “default” for dealing with fundamentally insecure, password-based authentication methods. We understand why they were the “go-to,” but hope to interrupt the “passwords are bad, so we need 2FA/MFA” refrain.
There is now a new option grabbing attention and gaining traction – Modern Passwordless Authentication. For our take on why the status quo needs to change, you can explore our blog: Is it finally time to kill traditional 2FA and MFA? We also discuss the ways traditional 2FA/MFA is vulnerable and provide examples in our blog: How Your MFA Can Be Hacked.
Let’s compare traditional 2FA/MFA against Beyond Identity’s Passwordless Authentication. We will take a look at them side-by-side across a few essential categories, including security, user experience, and compliance. These categories reflect the challenges shared between InfoSec teams and the account holders to ensure secure access, providing a good user experience, enabling rapid adoption.
Security
Traditional 2FA/MFA
Traditional 2FA/MFA solutions typically rely on a password as the first factor. Unfortunately, the second factor is often quite vulnerable.
Mobile device verification, using voice or text, is susceptible to SIM swaps, where a hacker tricks your carrier into switching over your phone line. These attacks are becoming increasingly common.
The one-time passwords (OTP) generated through 2FA/MFA can be hijacked and used by attackers who have access to a user’s email or SMS. These “one-time codes,” like passwords, are shared secrets that can be stolen and reused. OTPs can also be predicted by clever hackers. NIST has retracted its support for SMS-based MFA, and in November 2020, Microsoft urged users to stop using call & SMS-based multi-factor authentication.
Even the more secure 2FA/MFA approaches like push notifications, which use out-of-band channels, have their issues. Attackers now send multiple push notifications knowing that users, conditioned to clear them, will often approve them without thinking about the consequences – letting a bad guy in.
The second factor in traditional 2FA/MFAs merely inconvenience hackers but don’t do much to stop them.
Check out How Your MFA Can Be Hacked (With Examples) for a deeper dive into some of how traditional 2FA/MFA is vulnerable to attack.
Beyond Identity’s Passwordless Authentication
Our passwordless authentication fully eliminates the password. It does not hide the password behind another factor. Thus, there are no password databases for attackers to steal, and logins don’t rely on shared secrets of any kind. This approach stops credential stuffing, rainbow table attacks, and other password-based attacks in their tracks.
The most secure solutions rely on asymmetric cryptography for fundamentally secure authentication, rather than “symmetric,” shared secrets, like passwords, which are fundamentally insecure because they must be stored and known by both parties.
Beyond Identity uses a private key securely stored in a secure enclave or trusted platform module (TPM) on modern endpoint devices. The TPM signs a certificate with the private key that can be validated using the corresponding public key. The public key can be shared without any risk. We trust this model inherently and use the technology every day. TLS, the “lock in the browser,” ensures private data we exchange with servers remains private and secure. TLS employs X.509 certificates that are based on asymmetric cryptography and public-private key pairs.
Security is improved because there are no vulnerable passwords to steal, and the TPM housing the private key is not easily breached. According to a high-profile case from last January, even the U.S. Federal Bureau of Investigations has been unable to gain access to devices in their custody. These devices rely on TPM/enclaves and asymmetric crypto. Beyond Identity’s Modern Passwordless Authentication leverages X.509 certificates without the need for a certificate authority or any certificate management. It merely extends the Chain of Trust™ established by TLS to users and their devices.
Check out A Tale of Two Keys: The Simple Explanation of Passwordless for more of an explanation on asymmetric cryptography and how it’s used in passwordless authentication.
User Experience
Traditional 2FA/MFA
Barely half of Americans had bothered to set up traditional 2FA/MFA for even one account by the end of 2019, according to this article published by Dark Reading. Traditional 2FA/MFA is challenging to set up and adds friction to every login. First, users have to enter the password. Then they will have to access a second account, an app, or find their phone to verify themselves and complete the process.
In many consumer or workforce use cases, this means logging in to an email account or accessing the SMS on their mobile device. With one-time passwords (OTP) and “push notifications” – where an out-of-band signal is sent to an app on a mobile device and the user has to press the button to continue the login – the user will also have to locate and unlock their second device with each login. This traditional 2FA/MFA process, which is only incrementally more secure than a regular password login, creates significant and unwelcome inconvenience for end users.
Beyond Identity’s Passwordless Authentication
Modern passwordless authentication uses a new type of authenticator on the device to confirm user identity securely. The approach leverages the secure biometric (face or fingerprint) recognition technology built into modern endpoints.
This approach employs two authentication factors, something you are (biometric) and something you possess, the PC or mobile device you are logging in with. This form of multi-factor authentication is fundamentally secure. It provides a frictionless user experience since it does not require the user to pick up a second device or fish a code out of an SMS or email. Users love not having to memorize different passwords or change them periodically. Modern passwordless authentication provides extra security without the hassle of traditional 2FA/MFA.
Regulatory Compliance
Traditional 2FA/MFA
MFA has become the “go-to” option in many industries, but it’s typically not mandated in regulations. Most regulations (HIPAA and PCI, for example) simply require strong authentication. However, between regulators and auditor interpretation, traditional 2FA/MFA became a de facto standard. It was the only game in town and an easy-to-grasp concept when governments and industries were demanding more comprehensive authentication.
2FA/MFA got a boost a little over 15 years ago, when organizations such as the Federal Financial Institutions Examination Council (FFIEC) decried single-factor authentication as inadequate. They mentioned 2FA/MFA by name as a better alternative.
Beyond Identity’s Passwordless Authentication
Modern passwordless authentication solutions significantly improve security by removing weak factors (shared secrets) and leveraging multiple authentication factors so that auditors are completely satisfied. But these solutions can do this without frustrating end users and adversely impacting productivity. Organizations are deploying our passwordless authentication solution today because it passes auditor muster, and even Gartner® agrees that it is a robust alternative.
The Verdict
Providing strong authentication is an ongoing challenge that must balance comprehensive security against user experience. Traditional 2FA/MFA was a reasonable, if flawed, alternative for greater security in its day, but today the winner is clear. Beyond Identity’s Passwordless Authentication provides both a great user experience and a very high level of protection.
Explore Beyond Identity’s advanced Passwordless Identity Management Platform and learn how to provide a seamless, passwordless, multi-factor experience for both your workforce and customers. Also, explore Beyond Identity's passwordless MFA solution.
Traditional Two-Factor or Multi-Factor Authentication (2FA/MFA) remains the “default” for dealing with fundamentally insecure, password-based authentication methods. We understand why they were the “go-to,” but hope to interrupt the “passwords are bad, so we need 2FA/MFA” refrain.
There is now a new option grabbing attention and gaining traction – Modern Passwordless Authentication. For our take on why the status quo needs to change, you can explore our blog: Is it finally time to kill traditional 2FA and MFA? We also discuss the ways traditional 2FA/MFA is vulnerable and provide examples in our blog: How Your MFA Can Be Hacked.
Let’s compare traditional 2FA/MFA against Beyond Identity’s Passwordless Authentication. We will take a look at them side-by-side across a few essential categories, including security, user experience, and compliance. These categories reflect the challenges shared between InfoSec teams and the account holders to ensure secure access, providing a good user experience, enabling rapid adoption.
Security
Traditional 2FA/MFA
Traditional 2FA/MFA solutions typically rely on a password as the first factor. Unfortunately, the second factor is often quite vulnerable.
Mobile device verification, using voice or text, is susceptible to SIM swaps, where a hacker tricks your carrier into switching over your phone line. These attacks are becoming increasingly common.
The one-time passwords (OTP) generated through 2FA/MFA can be hijacked and used by attackers who have access to a user’s email or SMS. These “one-time codes,” like passwords, are shared secrets that can be stolen and reused. OTPs can also be predicted by clever hackers. NIST has retracted its support for SMS-based MFA, and in November 2020, Microsoft urged users to stop using call & SMS-based multi-factor authentication.
Even the more secure 2FA/MFA approaches like push notifications, which use out-of-band channels, have their issues. Attackers now send multiple push notifications knowing that users, conditioned to clear them, will often approve them without thinking about the consequences – letting a bad guy in.
The second factor in traditional 2FA/MFAs merely inconvenience hackers but don’t do much to stop them.
Check out How Your MFA Can Be Hacked (With Examples) for a deeper dive into some of how traditional 2FA/MFA is vulnerable to attack.
Beyond Identity’s Passwordless Authentication
Our passwordless authentication fully eliminates the password. It does not hide the password behind another factor. Thus, there are no password databases for attackers to steal, and logins don’t rely on shared secrets of any kind. This approach stops credential stuffing, rainbow table attacks, and other password-based attacks in their tracks.
The most secure solutions rely on asymmetric cryptography for fundamentally secure authentication, rather than “symmetric,” shared secrets, like passwords, which are fundamentally insecure because they must be stored and known by both parties.
Beyond Identity uses a private key securely stored in a secure enclave or trusted platform module (TPM) on modern endpoint devices. The TPM signs a certificate with the private key that can be validated using the corresponding public key. The public key can be shared without any risk. We trust this model inherently and use the technology every day. TLS, the “lock in the browser,” ensures private data we exchange with servers remains private and secure. TLS employs X.509 certificates that are based on asymmetric cryptography and public-private key pairs.
Security is improved because there are no vulnerable passwords to steal, and the TPM housing the private key is not easily breached. According to a high-profile case from last January, even the U.S. Federal Bureau of Investigations has been unable to gain access to devices in their custody. These devices rely on TPM/enclaves and asymmetric crypto. Beyond Identity’s Modern Passwordless Authentication leverages X.509 certificates without the need for a certificate authority or any certificate management. It merely extends the Chain of Trust™ established by TLS to users and their devices.
Check out A Tale of Two Keys: The Simple Explanation of Passwordless for more of an explanation on asymmetric cryptography and how it’s used in passwordless authentication.
User Experience
Traditional 2FA/MFA
Barely half of Americans had bothered to set up traditional 2FA/MFA for even one account by the end of 2019, according to this article published by Dark Reading. Traditional 2FA/MFA is challenging to set up and adds friction to every login. First, users have to enter the password. Then they will have to access a second account, an app, or find their phone to verify themselves and complete the process.
In many consumer or workforce use cases, this means logging in to an email account or accessing the SMS on their mobile device. With one-time passwords (OTP) and “push notifications” – where an out-of-band signal is sent to an app on a mobile device and the user has to press the button to continue the login – the user will also have to locate and unlock their second device with each login. This traditional 2FA/MFA process, which is only incrementally more secure than a regular password login, creates significant and unwelcome inconvenience for end users.
Beyond Identity’s Passwordless Authentication
Modern passwordless authentication uses a new type of authenticator on the device to confirm user identity securely. The approach leverages the secure biometric (face or fingerprint) recognition technology built into modern endpoints.
This approach employs two authentication factors, something you are (biometric) and something you possess, the PC or mobile device you are logging in with. This form of multi-factor authentication is fundamentally secure. It provides a frictionless user experience since it does not require the user to pick up a second device or fish a code out of an SMS or email. Users love not having to memorize different passwords or change them periodically. Modern passwordless authentication provides extra security without the hassle of traditional 2FA/MFA.
Regulatory Compliance
Traditional 2FA/MFA
MFA has become the “go-to” option in many industries, but it’s typically not mandated in regulations. Most regulations (HIPAA and PCI, for example) simply require strong authentication. However, between regulators and auditor interpretation, traditional 2FA/MFA became a de facto standard. It was the only game in town and an easy-to-grasp concept when governments and industries were demanding more comprehensive authentication.
2FA/MFA got a boost a little over 15 years ago, when organizations such as the Federal Financial Institutions Examination Council (FFIEC) decried single-factor authentication as inadequate. They mentioned 2FA/MFA by name as a better alternative.
Beyond Identity’s Passwordless Authentication
Modern passwordless authentication solutions significantly improve security by removing weak factors (shared secrets) and leveraging multiple authentication factors so that auditors are completely satisfied. But these solutions can do this without frustrating end users and adversely impacting productivity. Organizations are deploying our passwordless authentication solution today because it passes auditor muster, and even Gartner® agrees that it is a robust alternative.
The Verdict
Providing strong authentication is an ongoing challenge that must balance comprehensive security against user experience. Traditional 2FA/MFA was a reasonable, if flawed, alternative for greater security in its day, but today the winner is clear. Beyond Identity’s Passwordless Authentication provides both a great user experience and a very high level of protection.
Explore Beyond Identity’s advanced Passwordless Identity Management Platform and learn how to provide a seamless, passwordless, multi-factor experience for both your workforce and customers. Also, explore Beyond Identity's passwordless MFA solution.








.avif)
.avif)
.avif)

.avif)
.avif)



.avif)






.avif)

