The only identity platform built to eliminate, not just reduce, identity and device-based threats.

.svg)







.svg)







Dare to do identity differently
Phishing-Resistant MFA
Eliminate phishing and MFA bypass attacks.
Device Trust
Secure your entire fleet, even on unmanaged devices.
Secure SSO
Maintain user productivity, eliminate identity-based attacks.
RealityCheck
Prevent deepfake fraud in corporate meetings and chats.
Secure Access Platform
The only IAM platform that eliminates identity-based attacks with continuous, phishing-resistant access controls.
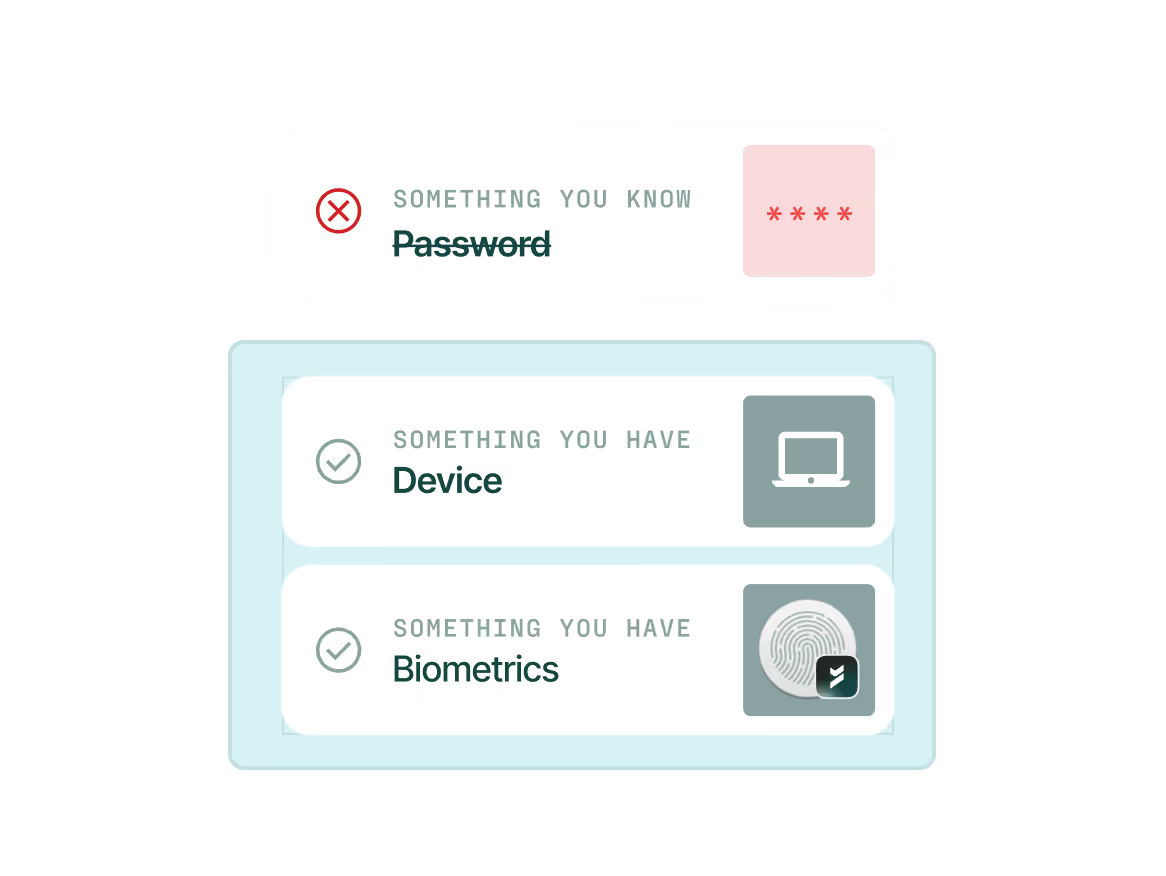
Remove shared secrets
Secure access using passwordless, phishing-resistant MFA that never falls back to phishable factors like SMS or TOTP that are easily phished or replayed.
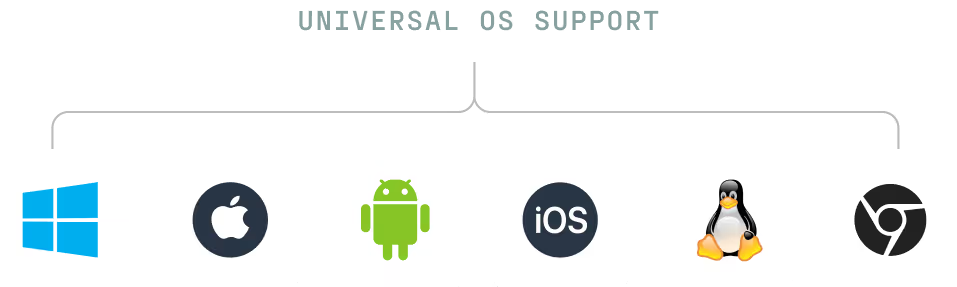
Secure all devices, any OS
Protect your entire fleet, including BYOD, contractor, and unmanaged devices with universal OS support.
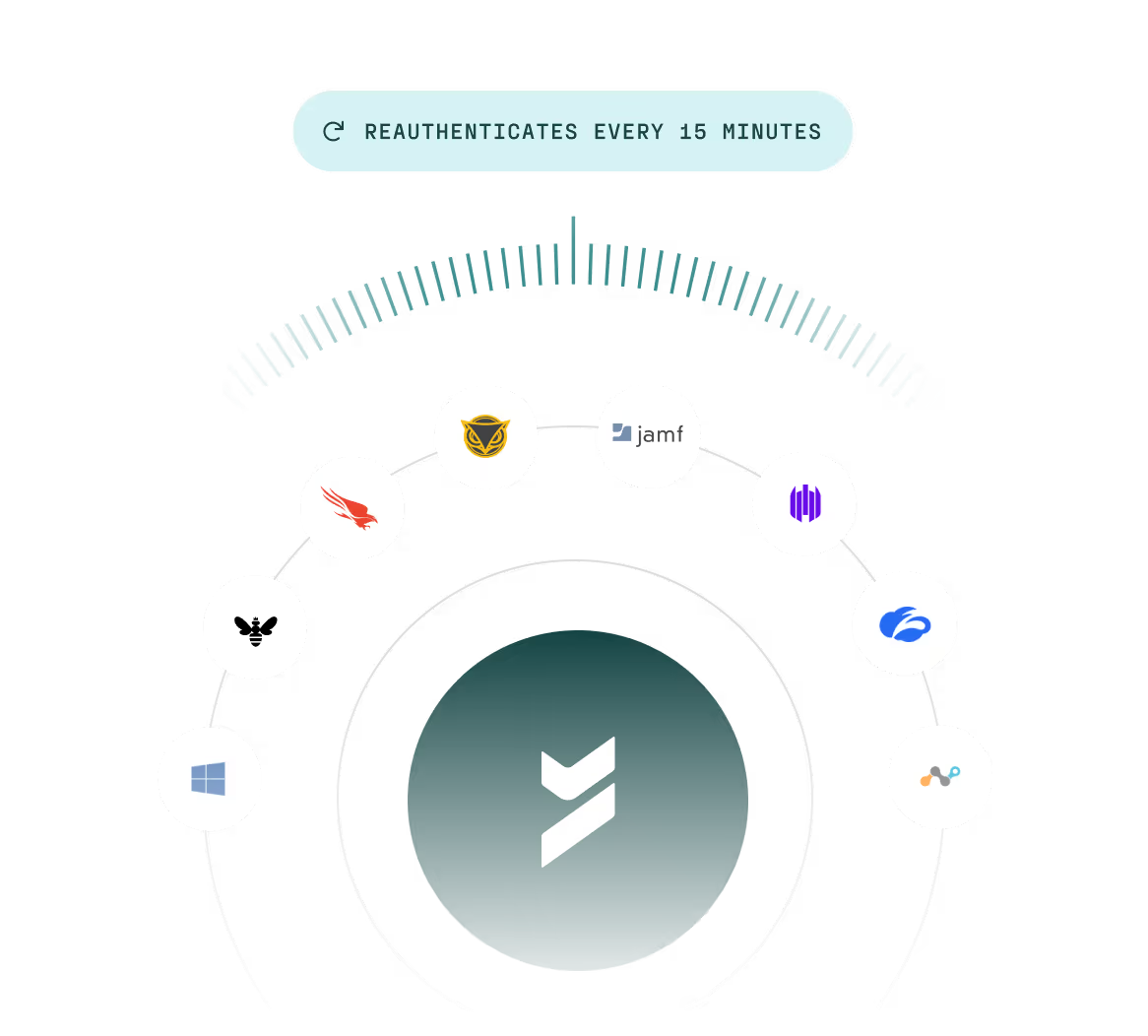
Authenticate continuously
Continuously enforce real-time user and device posture to identify and stop threats as they emerge.
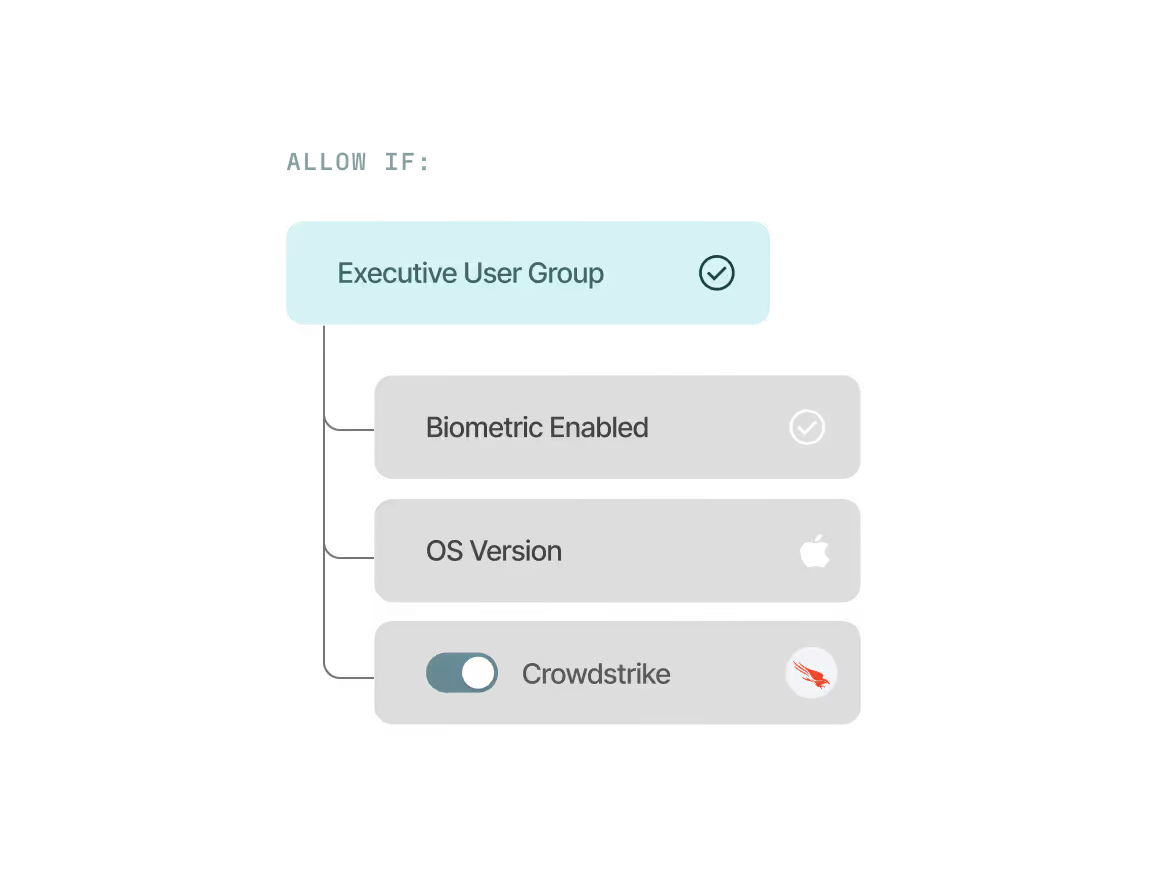
Enforce precise access controls
Easily configure granular, adaptive adccess policies with per app, OS, and user group controls. Simply integrates with your EDR, MDM, and ZNTA tools.
Maximum security.
Unmatched UX.
Deliver faster, simpler logins for users.




.avif)

.png)

.png)
.jpg)
.png)


.jpg)

.jpg)



.jpg)

.jpg)


